
Hello everyone,
After successfully completing the API penetration testing course from APIsec University, I practiced API testing skills on various platforms and encountered the topic of testing for SSRF vulnerabilities in APIs. This blog aims to explain how to search for SSRF in APIs.
What is SSRF?
Server-Side Request Forgery (SSRF) is a vulnerability that takes place when an application retrieves remote resources without validating user input. An attacker can supply their own input, in the form of a URL, to control the remote resources that are retrieved by the targeted server. This allows an attacker to gain access to sensitive data or even leads to application compromises.
Types of SSRF:
- In Band SSRF: The attacker can send requests to the internal network and the result is sent directly back in the response itself.
- Blind SSRF: It occurs if the attacker can cause an application to issue a back-end HTTP request to a supplied URL, but the response from the back-end request is not returned in the response
Testing:
To test for SSRF vulnerability, look for endpoints that involve user inputs that retrieve resources from the server, full or partial URLs in the POST body or parameters, headers, and endpoints that fetch content from another URL.\
We are testing an intentionally vulnerable web application called VAPI. If you wish to test VAPI on your local machine, you can access their GitHub repository here.
Commands to install VAPI:
git clone https://github.com/roottusk/vapi.git
cd vapi
sudo docker compose up -d
You can access the VAPI app from a local browser at: http://127.0.0.1/vapi
After successfully installing VAPI, add VAPI collections in Postman. Open Postman, click on import and drag and drop VAPI collections from the /vapi/postman folder.
In the Postman collection, navigate to the “Arena” folder. We are going to test the serversurfer.
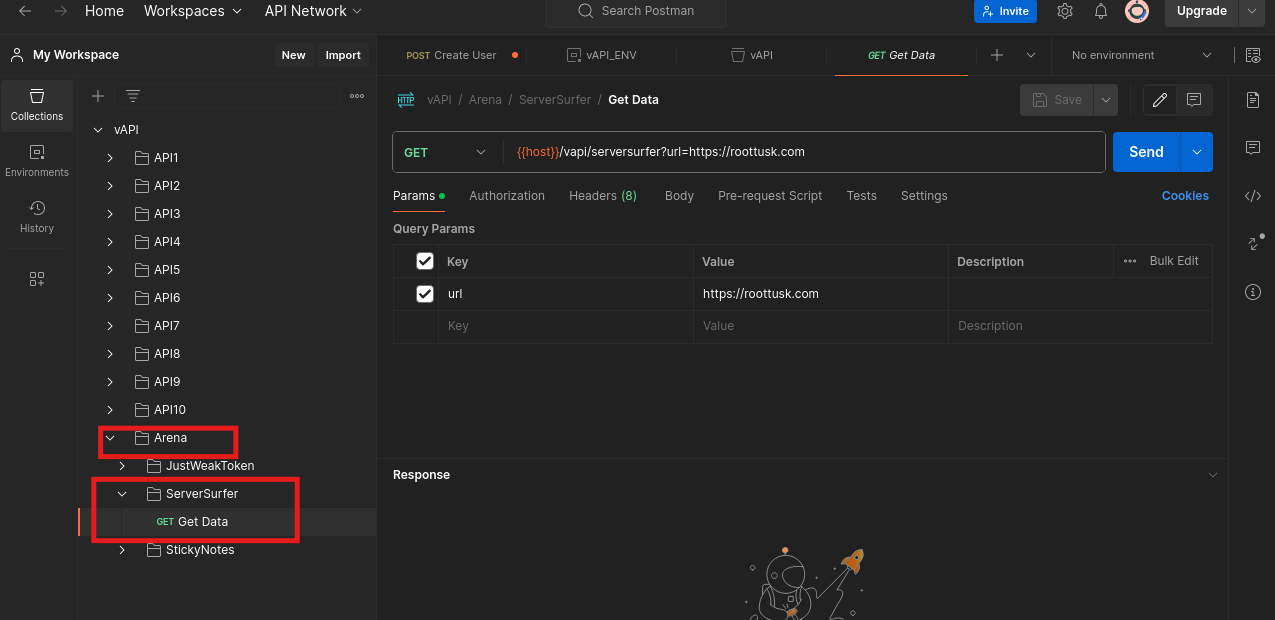
Look at the GET data request, which includes a URL that fetches content from another URL. Click on “SEND.”
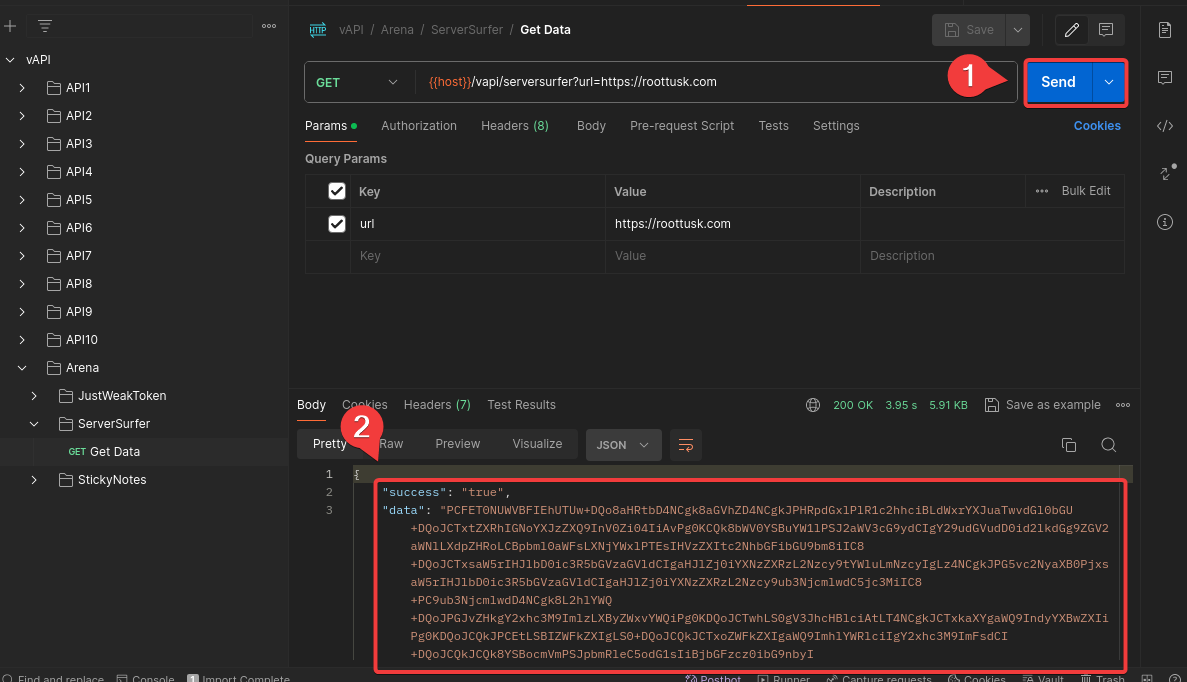
Upon sending the request, you will notice some JSON data in the response header that includes a string named data with some lengthy base64 encoded text. Decoding this text results in HTML code.
Next, try adding another URL. Here, I am using webhook. Visit the webhook site, click on edit, add content as “hacked,” and click “save.”
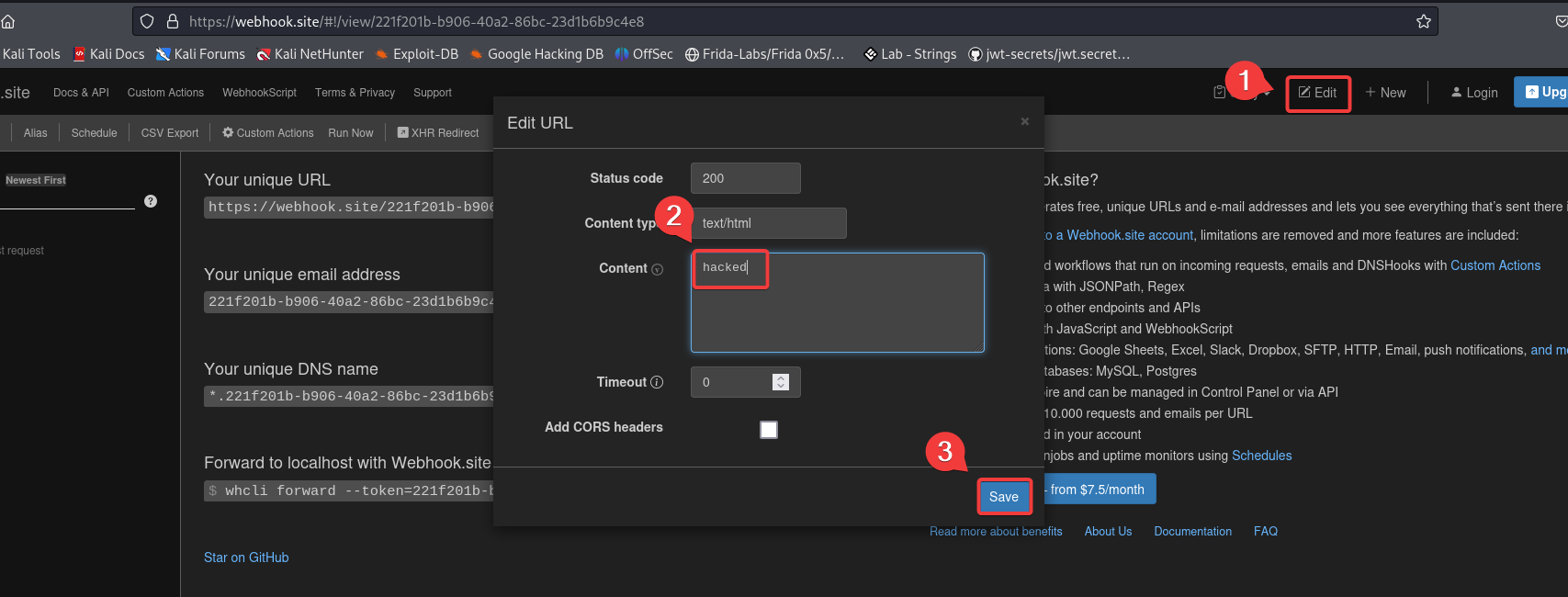
Copy the unique URL from the webhook.
Return to Postman and change the value of the GET request to our webhook URL.
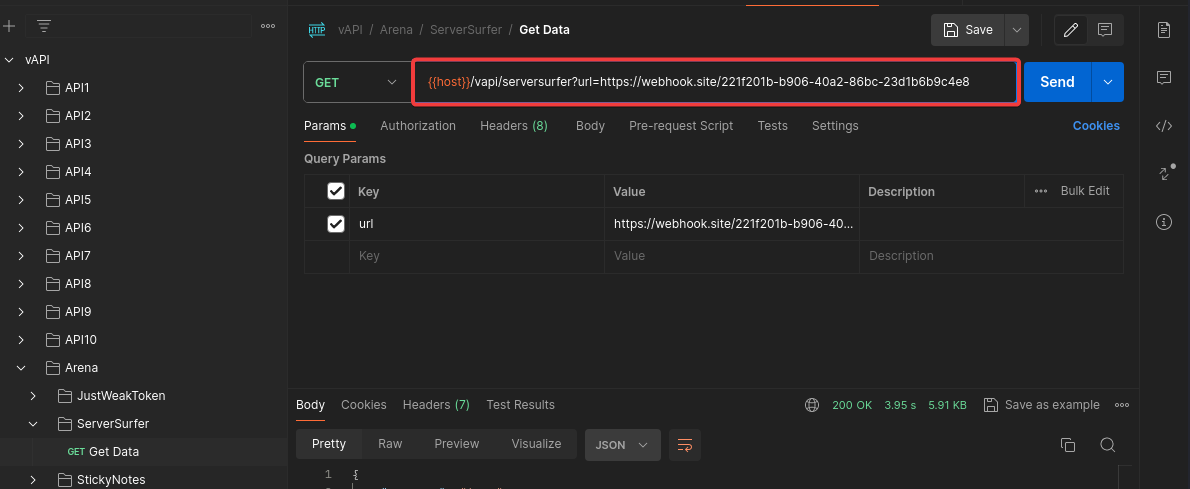
Click “SEND.” After sending the request, observe that the content of the data field in the response has changed. Decode the base64 string.
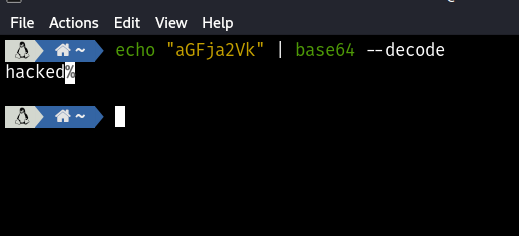
As you can see, the text we entered in the webhook is reflected in the response. This demonstrates a simple example of In-band SSRF.
In the case of Blind SSRF, the content in the response body is not visible. Instead, if you check the webhook, you will notice that the GET request was successfully sent to our webhook URL.
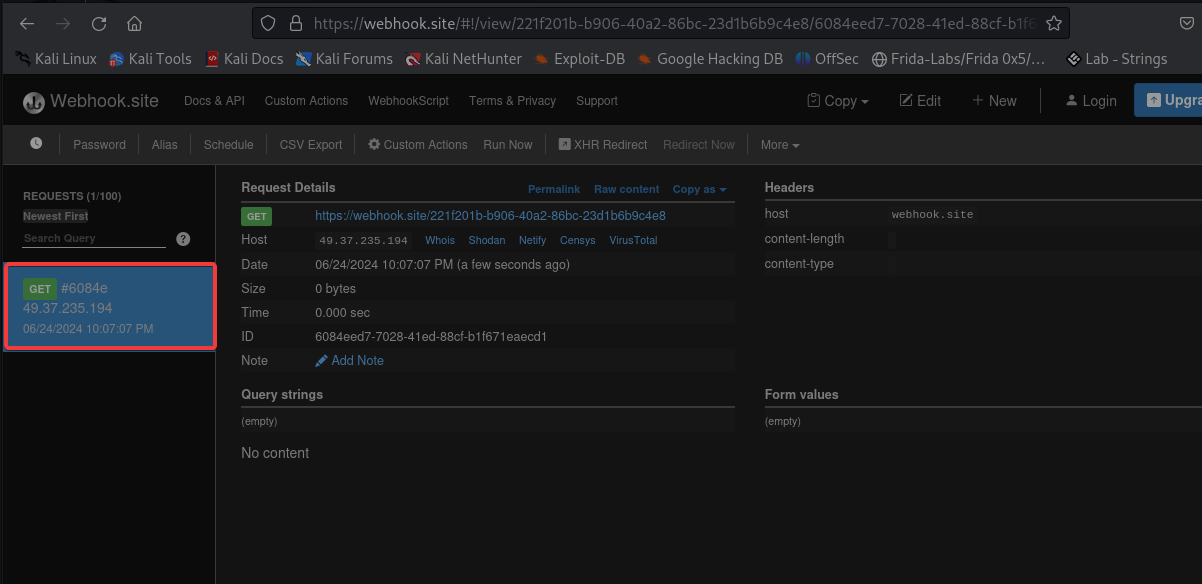
NOTE: This example provides a straightforward demonstration of SSRF. In reality, it may not be as simple.
Happy Pentesting ..!