
Hello guys,
Welcome back to my blog, where today we will delve into the realm of Android vulnerabilities. In a previous post, I discussed how to set up an Android lab environment to kickstart your pentesting career. Now, let’s focus on some commonly encountered vulnerabilities found in Android applications.
We will be testing an intentionally vulnerable app known as Insecure Shop. Please note that this is not a step-by-step guide for the app. My goal is to help you understand some common vulnerabilities in Android apps.
Insecure Logging.
Insecure logging occurs when sensitive data such as passwords and tokens are unintentionally stored in the device’s memory. Developers often use this method for testing and debugging purposes. However, if they fail to remove this information before releasing the application into production, other apps or attackers can access and retrieve these logs, potentially compromising sensitive data.
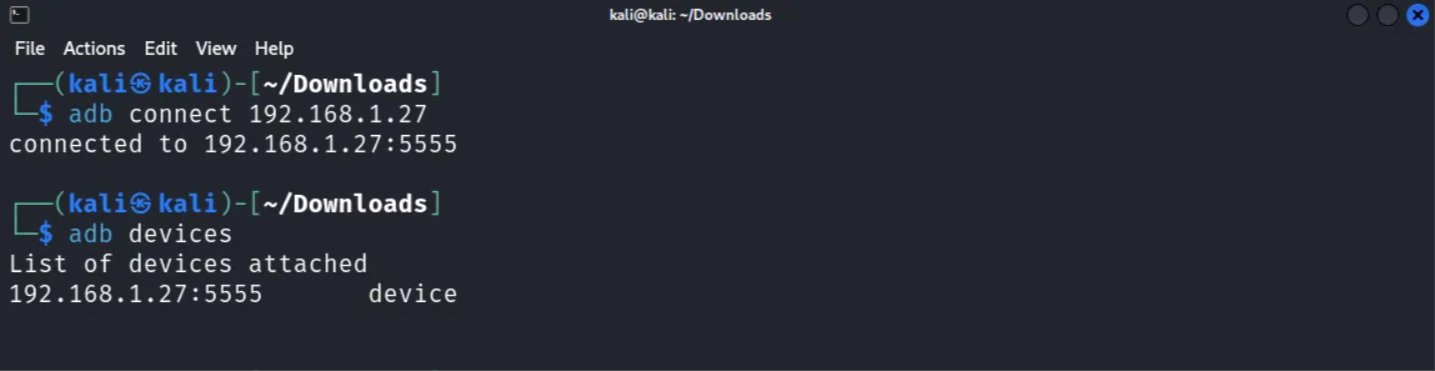
Let’s move on to the challenge and explore this vulnerability further. Before proceeding, make sure your Genymotion environment is connected to ADB by typing the following command:
adb connect $IPaddress
adb devices
Now, let’s open the application.

Upon opening, you will see a screen that asks for a username and password. To monitor device logs, you can open your Kali terminal and enter the command adb logcat.Logcat is a tool that records system messages, including errors, and any messages generated by your application using the Log class. Try entering a random username and password, and observe how they are logged within the logcat shell.
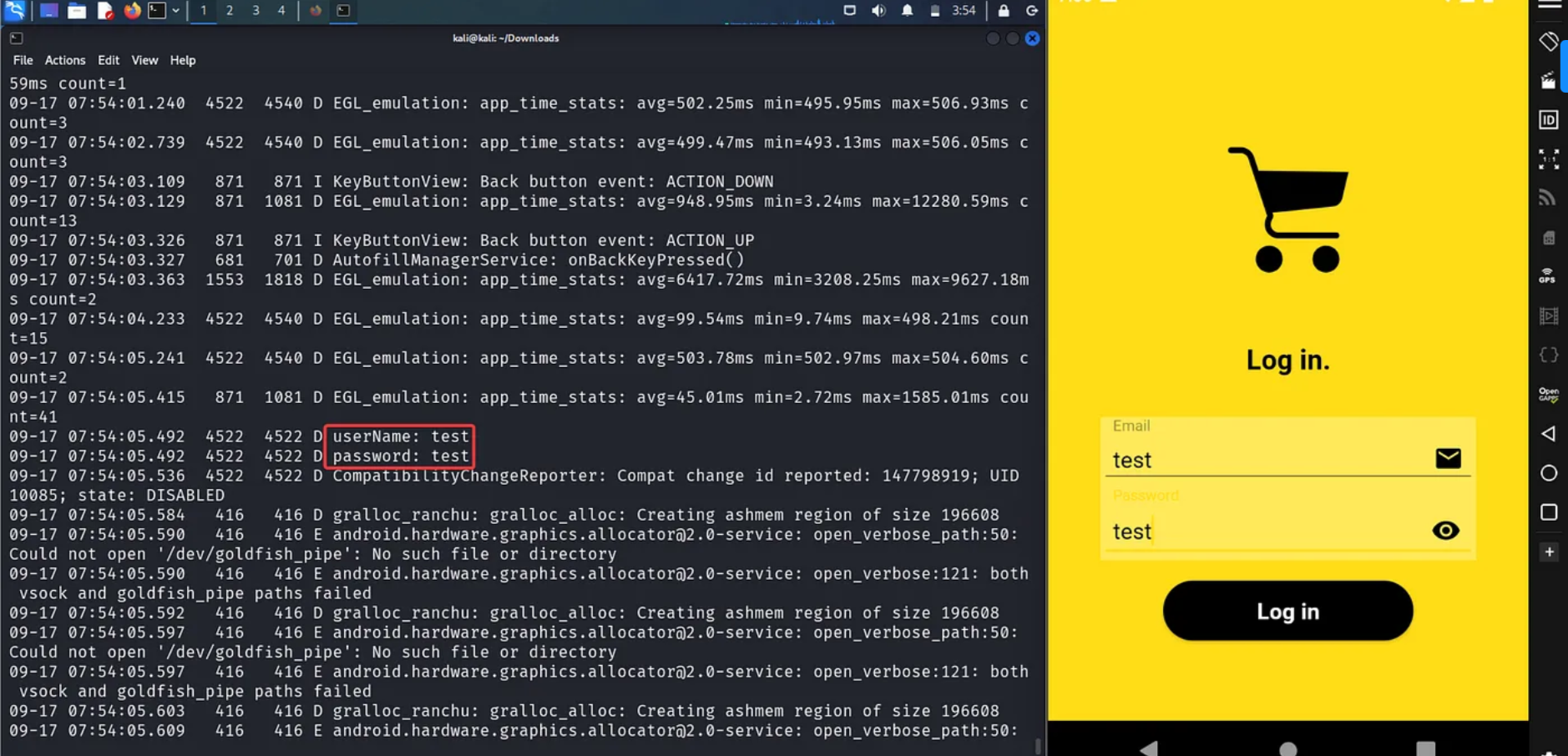
Hardcoded Credentials.
Another commonly encountered vulnerability is hardcoded credentials, where sensitive information such as usernames and passwords is directly embedded into the source code of an APK (Android Application Package). To extract data from an APK, we can use tools like apktool and JADX-GUI.
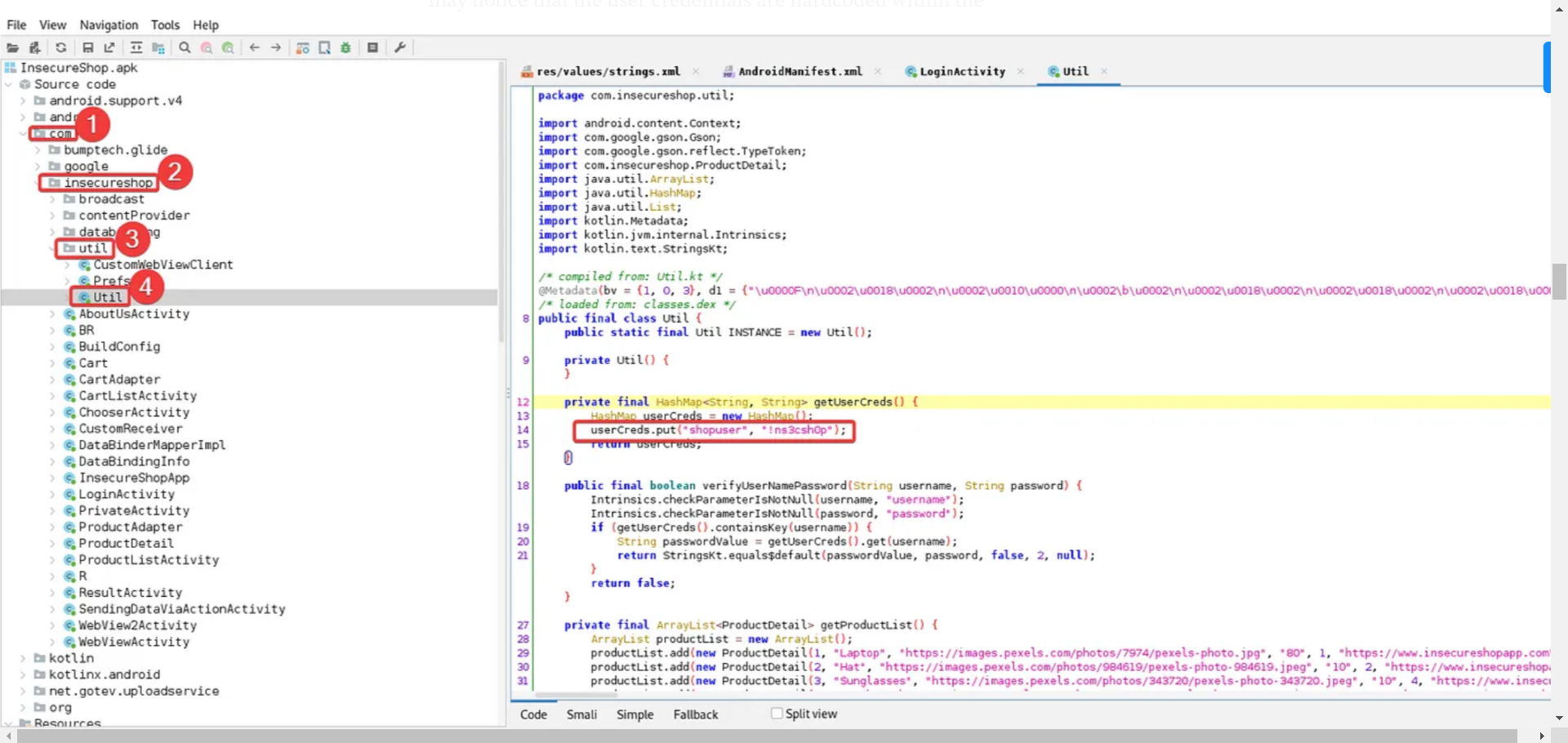
To open JADX-GUI, you can simply enter jadx-guiin the terminal. This tool allows us to extract information from the APK and view decompiled code.

Once you’ve opened JADX-GUI, navigate to the “util.util”. In this class, you may notice that the user credentials are hardcoded within the “getUserCreds” method. This means that valid account information is directly embedded in the code, allowing anyone with access to the code to log into the app using these credentials.
Insecure Data Storage.
Insecure data storage vulnerabilities arise when applications store sensitive information (e.g., usernames, passwords, credit card numbers) in plain text. To secure this data, strong security mechanisms should be implemented.
Let’s return to jadx-gui and double-click oncom.insecure.LoginActivity. You’ll notice a new tab that appears
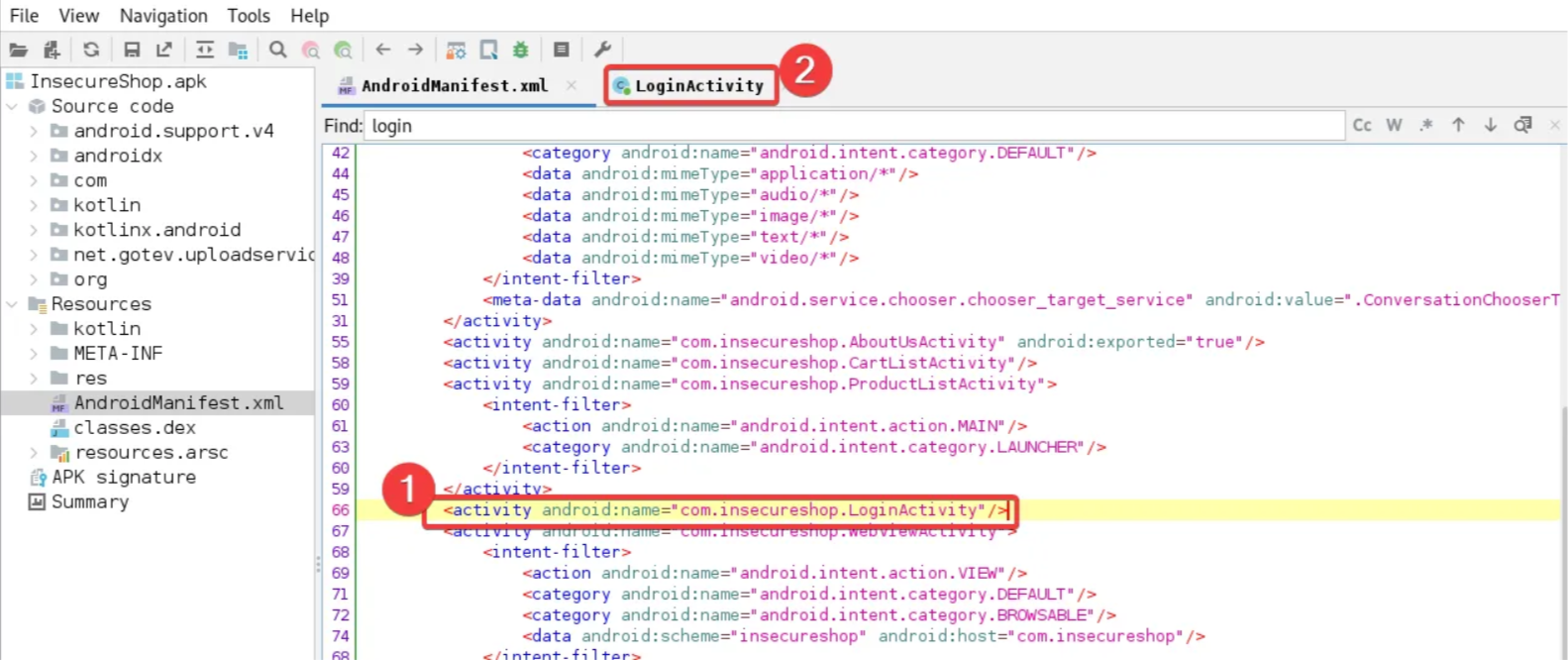
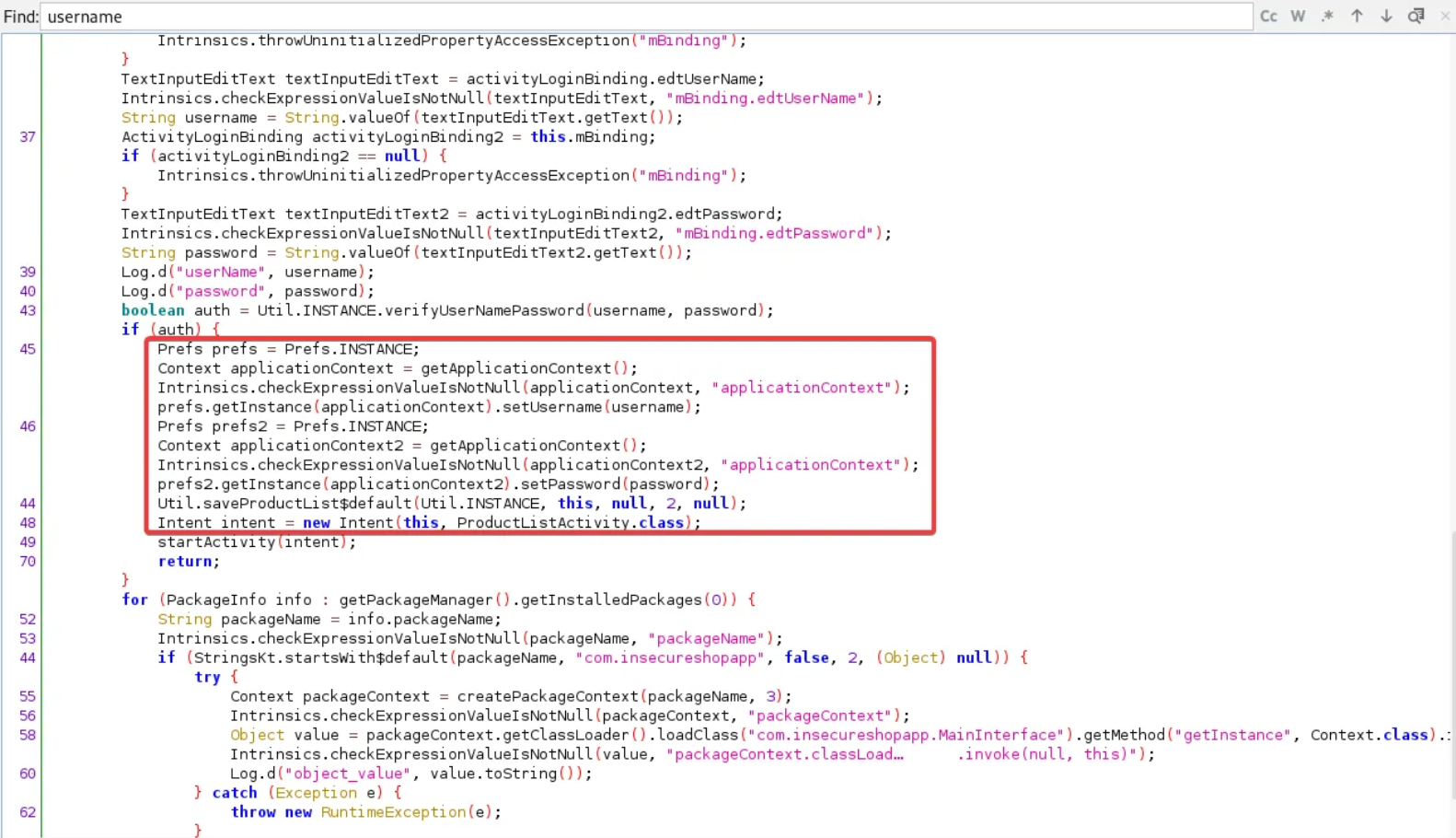
If we go tocom.insecure.LoginActivity and scrolling down, we can find a code snippet that saves the username and password values in the app’s shared folder.

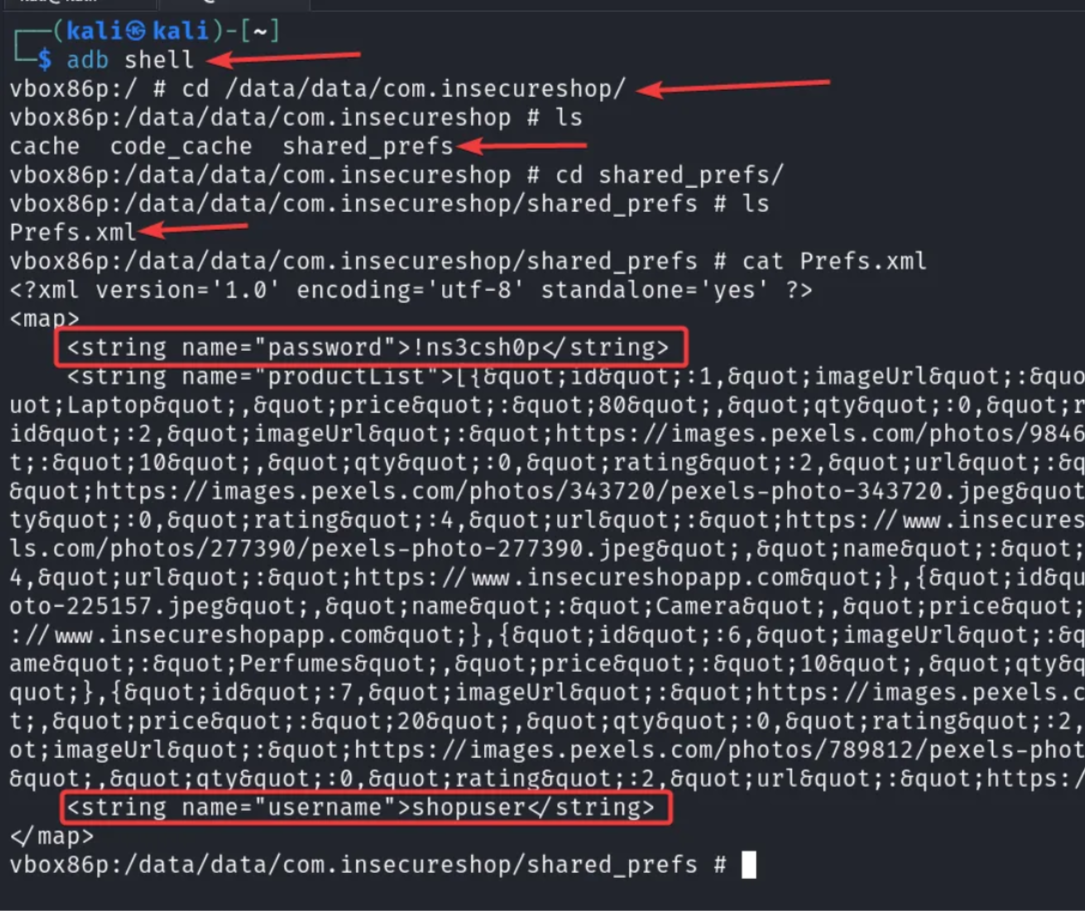
By entering adb shell. in the terminal, you can access the file system of the Android device. After that, you can access the shared preferences folder by entering the following command
cd /data/data/com.insecureshop/shared_prefs
Insecure URL validation is a serious problem that occurs when an Android application fails to properly validate or sanitize URLs before using them for network requests. This vulnerability can open the door to various security risks, such as Man-in-the-Middle (MITM) attacks and unauthorized URL redirection.
In this demonstration, we will exploit a vulnerability known as Deep Link Exploitation. If you are unfamiliar with deep links, you can learn more by clicking on the provided URL
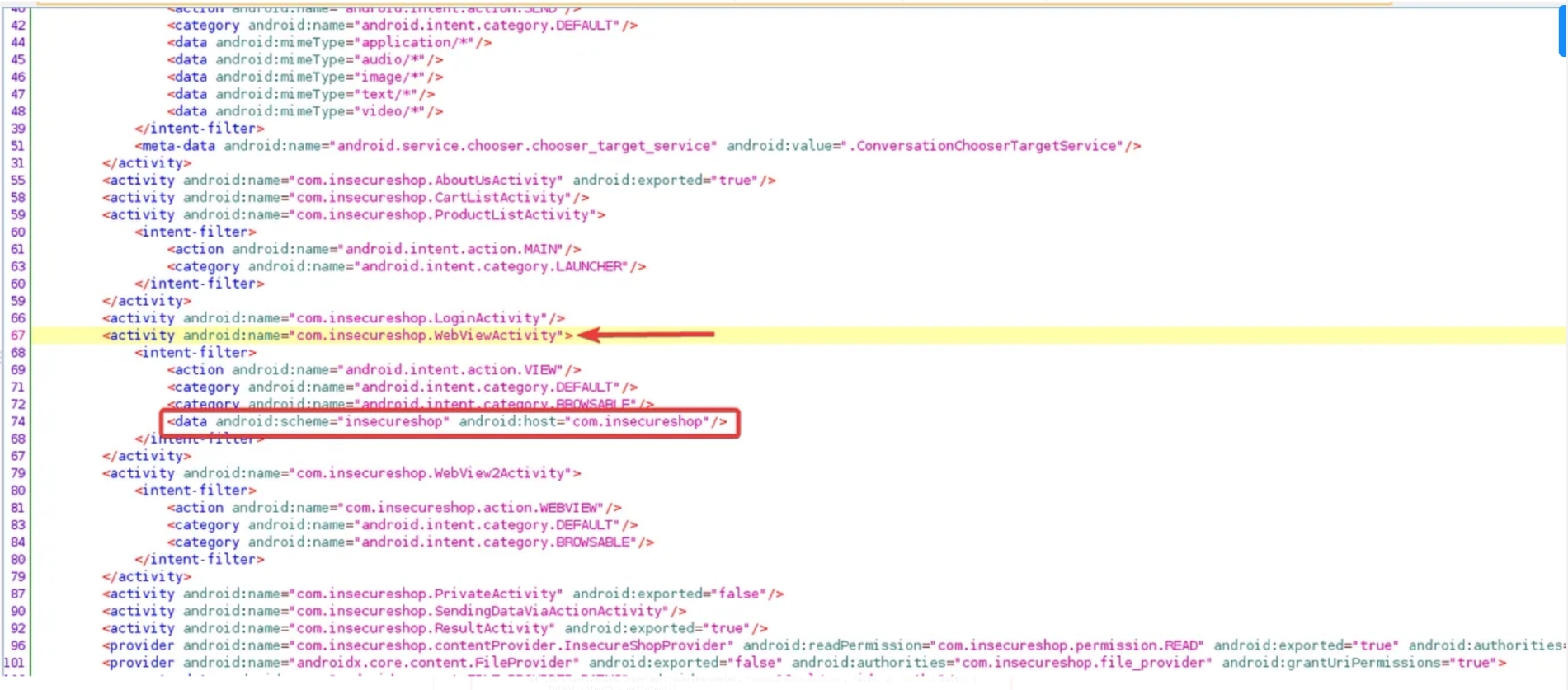
Open the AndroidManifest.xml and search for “webview”.
Take note of the scheme and host attributes. By holding the control key and clicking on com.insecureshop.webViewActivity, you will access the WebViewActivity code.
When examining the code, you’ll notice a validation check that ensures the URI path is set to “/web.” After this check, the “URL” parameter is extracted from intent and then loaded into a webview.
This enables the creation of a custom URI, where we can insert any parameter as a URL. To do this, we will use the following command:
adb shell am start -a android.intent.action.VIEW -d "insecureshop://com.insecureshop/web?url=https://google.com"

By executing this command, the application will load the arbitrary URL we provided. in this case google.com.
Conclusion
In this blog post, we explored common vulnerabilities found in Android applications. We discussed insecure logging, hardcoded credentials, insecure data storage, and input validation issues. It is crucial for developers and security tester to address these vulnerabilities and implement proper security measures to protect sensitive data.
Happy pentesting!