
Hello Friends,
In this blog, I will walk you through the practical steps to install the necessary tools for Android pentesting. By following this guide, you will be able to set up your lab environment and capture traffic using Burp Suite. So, let’s get started!
Installing ADB
ADB (Android Debug Bridge) is a command-line tool used for interacting with and managing Android devices or emulators.
To begin, open your Kali terminal and enter the following command to install ADB:
sudo apt-get install adb
Next, let’s install APKTool, which allows us to reverse-engineer Android APK files. Execute the following command:
sudo apt-get install apktool
Installing JADX
Jadx is a command-line tool used for decompiling and analyzing Android application (APK) files to retrieve their source code in a readable format. Before installing JADX-Gui, we need to install Java. Simply type the command:
sudo apt-get install default-jdk
After installing Java, proceed with the installation of JADX
sudo apt-get install jadx
We need to install a few more tools before setting up our emulator.
Frida-tools is a dynamic instrumentation toolkit used for analyzing and manipulating software applications at runtime
Execute the following command to install Frida Tools:
pip3 install frida-tools
Install Objection
Objection is a runtime mobile application exploration tool that helps security researchers and penetration testers analyze and manipulate Android and iOS apps by injecting custom scripts and interacting with them during runtime. Let’s install Objection by entering the following command:
pip3 install objection
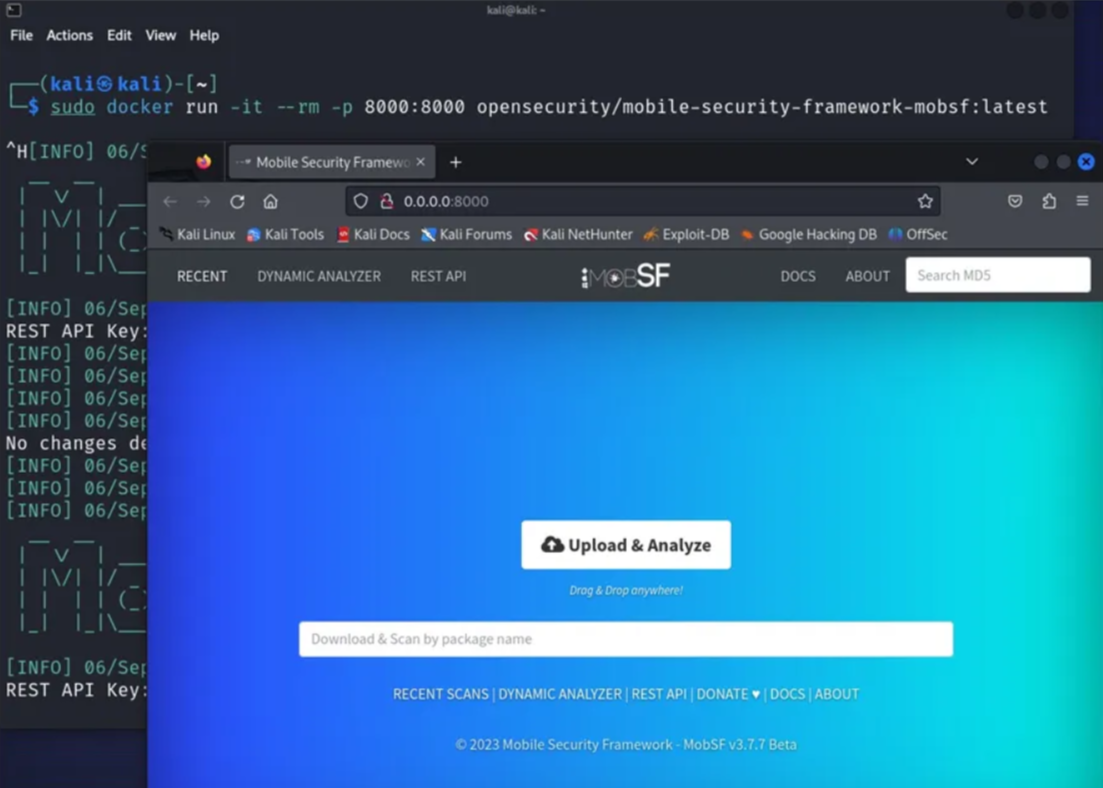
Installing MobSF using Docker
MobSF, short for Mobile Security Framework, is an open-source tool for mobile application security assessment and testing. It helps identify vulnerabilities and potential security issues in mobile apps
To install MobSF, we will use Docker and follow the step-by-step process given below:
Step 1: Install Docker
sudo apt install docker.io
step 2: Install MobSF
sudo docker pull opensecurity/mobile-security-framework-mobsf
step 3: Run MobSF
sudo docker run -it --rm -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
Emulator Setup
An Android emulator is a software-based simulation of an Android device that allows developers and users to run and test Android applications on a computer without the need for physical devices.
To proceed with the emulator setup, follow the steps below:
Step 1: Download Genymotion:
Download Genymotion for your Windows machine from here.
Step 2: Installation:
After downloading, install Genymotion and open the application. If you are a registered user, use your credentials to log in. If not, create a new account and log in.
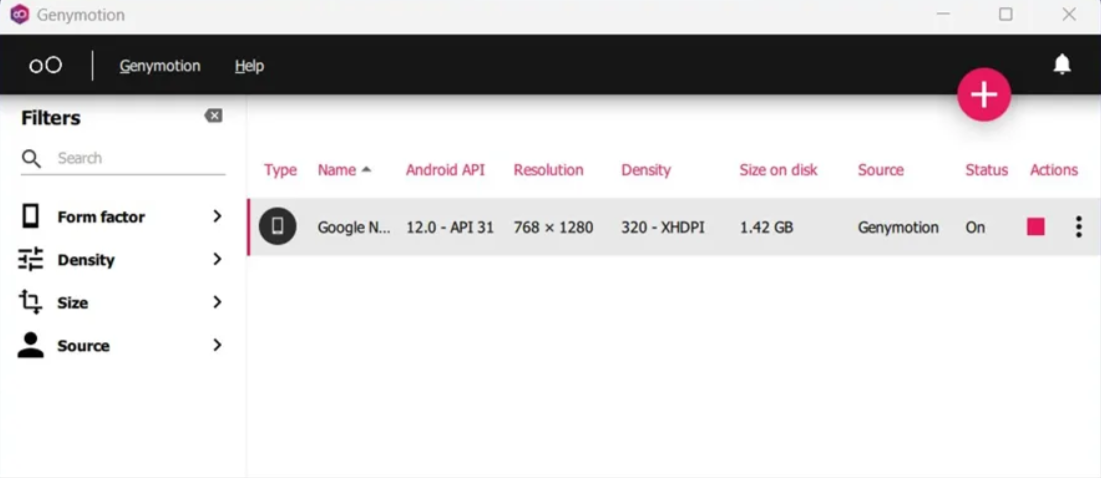
Step 3: Emulator Configuration:
In the Genymotion app, you can see that I already have one emulator running. You can add a new emulator by clicking the plus icon, selecting a device, and installing it. Ensure that the emulator is set to the bridged adapter to connect it to our Kali machine.
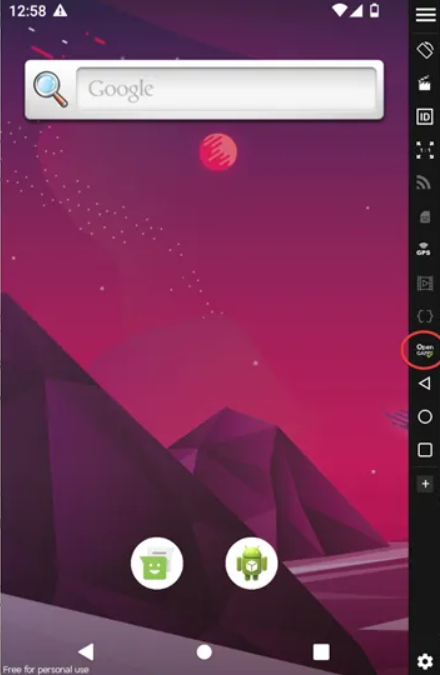
Step 4: Launching the Emulator:
Once everything is set up correctly, launch the emulator. By default, Genymotion does not have the Play Store installed. To install it, click on the Gapps icon.
Burp Suite Configuration
To capture traffic using Burp Suite, follow these steps:
Step 1: Burpsuite configurations.
Kali Linux Configuration:
Open Burp Suite and go to the Proxy tab. Select “Proxy Settings” and click on “Add” under the Proxy Listeners section.
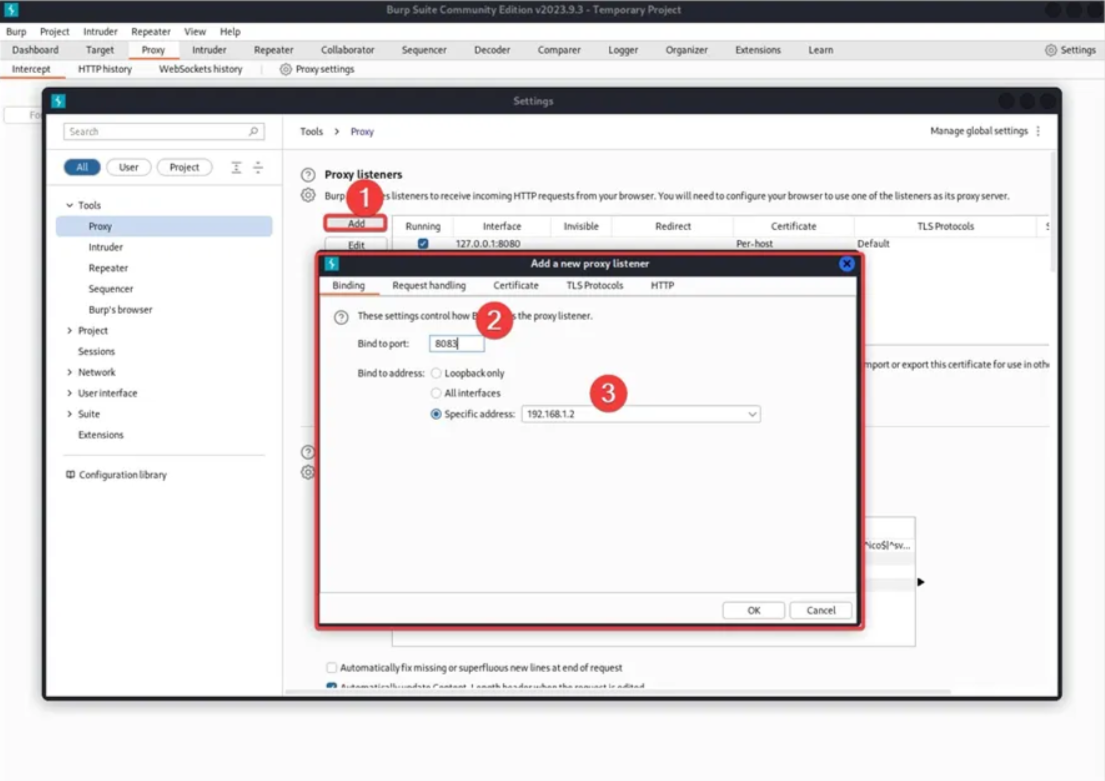
Android Device Proxy Configuration:
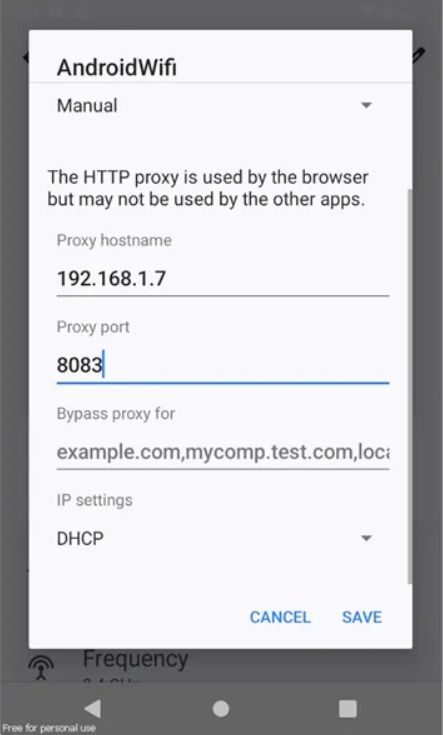
On your Android emulator, open the Wi-Fi settings and long-press the connected Wi-Fi name. Select the “Modify Network” option. Under the Proxy settings, choose “Manual” and enter the IP address of your Kali machine.
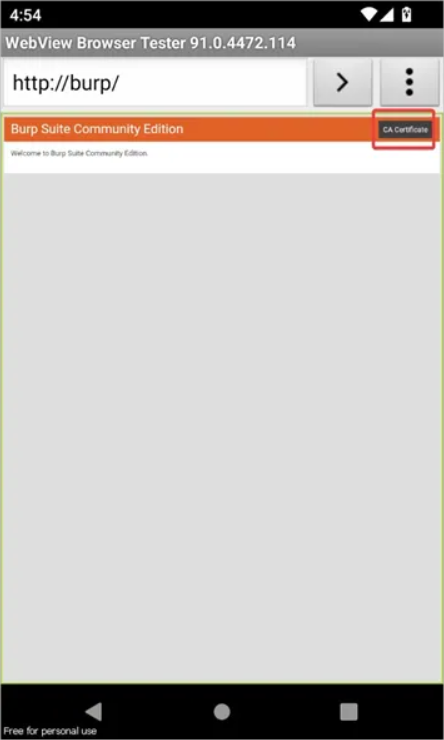
Step 2: Installing Burp Certificate in android emulator:
Open any browser on your Android device and browse to http://burp, Click on the CA Certificate to download it into the Downloads folder.
You can also transfer the CA certificate from the Kali machine to your emulator using the ADB tool. Just follow the command shown below:
adb push /downloads/cacert.der /sdcard/cacert.cer
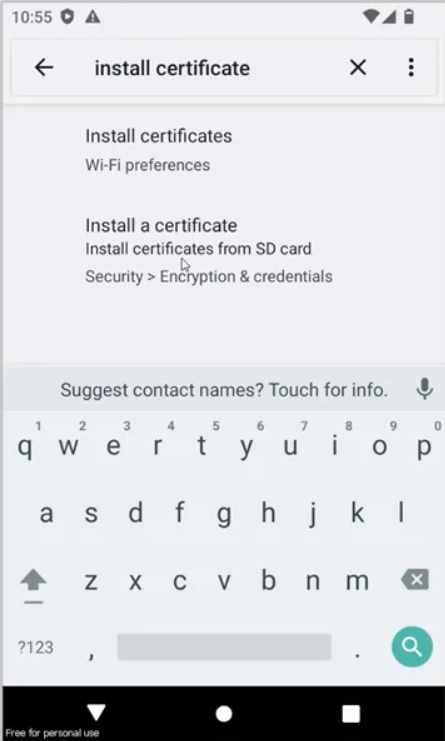
Step 3: Modify the Certificate Extension:
Change the file extension from .der to .cer. Then, navigate to the mobile settings, search for “Install Certificate,” and proceed accordingly.
By completing the installation of the required tools and configuring Burp Suite with your emulator, you are now equipped to start your mobile pentesting career. Remember, there are numerous other tools available for mobile pentesting, but the ones covered in this practical guide are essential to get you started. Check out each tool and explore its various applications. For additional tools, feel free to visit the links below.
- Dex2jar: Converts .dex files to .class files, zipped as a jar file.
- Drozer: drozer is the leading security testing framework for Android.
- Ghidra: A software reverse engineering (SRE) suite of tools developed by NSA’s Research Directorate in support of the Cybersecurity mission.
- Gmaps scanner : Used for determining whether a leaked/found Google Maps API Key is vulnerable to unauthorized access by other applications or not.
- Keyhacks : It shows ways in which particular API keys found on a Bug Bounty Program can be used, to check if they are valid.
- Pidcat : logcat colour script which only shows log entries for processes from a specific application package
Okay, that’s it for now; I hope you found it informative.
Thank you.
Happy Pentesting!